Since first emerging in January of 2018, the GandCrab ransomware variants have affected more than 1.5 million users of the Windows Operating System, and the cyber criminal organization claiming they received more than $2 billion in ransomware extortion payments.
GandCrab ransomware
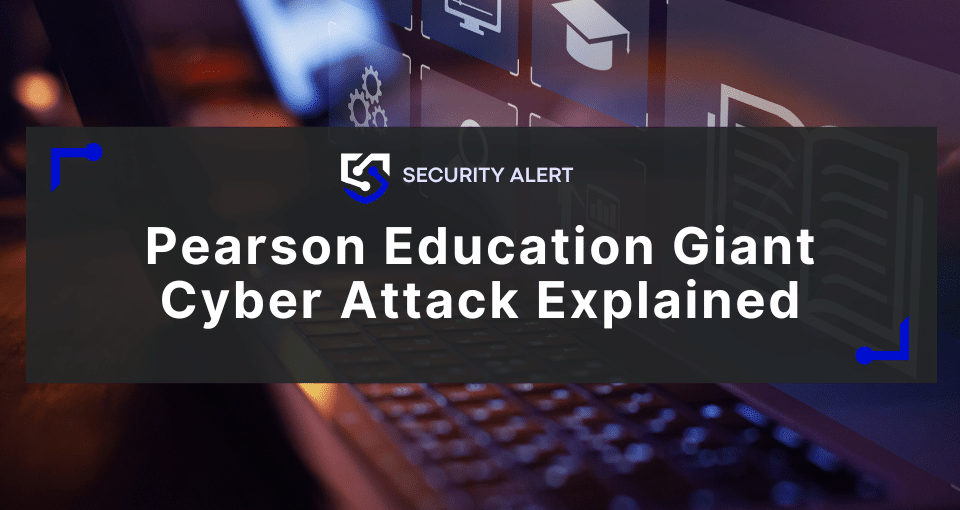
In June of 2019, the organization behind the infamous ransomware GandCrab announced in an online forum that they are ceasing operations and will not be providing any further decryptions and variants. First released on January 28, 2018, GandCrab ransomware is considered to be one of the most largely distributed ransomware variants globally, affecting both small businesses and large enterprises alike.
GandCrab ransomware has demonstrated the persistence and dexterity of global cyber criminal organizations and their will to keep the extortion business model in operation. Throughout the course of 2018, cyber security experts had developed working decryptors that removed encryption for early versions of the GandCrab ransomware. Over time, the creators of GrandCrab constructed new adaptations that rendered these free decryption tools useless. The creators of the GandCrab ransomware depicted such technological endurance that kept them ahead and in the extortion business for over a whole calendar year.
A post via an online forum Exploit.in showcases the group’s intentions of ceasing operation (via Bleeping Computer)
The GandCrab business model
One of the reasons the GandCrab cyber extortionists were able to affect so many businesses and organizations is due to the nature in which the ransomware was spread. The cyber criminals used a distribution model that allowed low-skilled malicious actors to buy and re-distribute ‘exploit kits’ of the ransomware variant to other organizations. As a result, the affiliate program and power of this distribution system advances the cycle.
With this model, it allowed the various stakeholders in the business to focus on specific functions and keep the ransomware in operation. Developers of the ransomware could focus their attention on creating new extensions and extortion programs while affiliate organizations utilized the ransomware programs to inflict encryption programs on victim’s computers and servers. As a result, GandCrab ransomware group claims they extorted more than $2 billion in ransom payments (although some experts say this number is inflated). GandCrab is known for this ‘Ransomware-as-a-service’ model which is becoming a widely adopted strategy among cyber criminal groups. These cyber criminal organizations are becoming more complex and organized, a much more modern approach to the early days of data extortions.
Final GandCrab decryptor released (Updated July 2019)
In light of the major announcement from the GandCrab criminal organization, public-private initiatives from coalition’s such as No More Ransom continue to host the most current decryptor tools available for free to the public. BitDefender, in partnership with, Romanian Police, DIICOT, Europol, FBI, NCA the Metropolitan Police, as well as Police Offices in Bulgaria and France, lead a program to obtain the decryption keys through the command & control center of the GandCrab ransomware. The result is a free tool that functions to decrypt files for any variants of GandCrab version 1, 4, and between 5 and 5.2.
FBI releases master decryption keys
On July 15, the FBI Cyber Division officially released Alert Number MC-000105-MW which includes encryption keys that help current victims of GandCrab ransomware to decrypt their files. The FBI has posted this issue under Traffic Light Protocol (TLP) White label which allows free distribution, accessibility and usage for the general public. Here are the master decryption keys for GandCrab versions 4, 5, 5.0.4, 5.1, and 5.2:
BwIAAACkAABSU0EyAAgAAAEAAQC77wJGC16Mco6goDGulTOC1meJMrLtkqgWCrwowU0+AKPcSEc96ZrBMa5BxegicGp/dZiPxuvuZZsbltNNqj91C6V153HNiKB34MsvM6INq+TjQII/2ZVQpJJWqndhBXXyJYHaob4wp8vaK6OehasDjbvT8LuccZrUmM/GwqhihDKFTBss/+TY2eUquxgGCGr02NGNAONB/OfFICXS3Uf/JwkfbTRsigrrqxNICfYkJJiEIt3BoRxgYwZx7gBKIbofr0wD0sc/umQ5NbRECxdftSyMTrLmYbIjIU2t+9Qdlkuh/H+/mHi703Lx40YfA0wFGJbBR8CgbxcHERArLdTIeb+0g3U9aGAzu6R6yFJmLub6RDJKrgarWp++KR09uKbAygsQOKRSJ7phrAo7DoaPeq+6iZ1KUjOBdGveYSaltFOlSEeOqNcBCKXf8gbd1UXc8+Cty/0eVSwIY+LwWzmBdVD7XH42LBO9j2/irryjHQ2WLZGI5I854JlxCeDjgO7TV++RUzxdADB8ewANZih+yepnGK7SwrYl3aS3HZJ6U6G706Ix+C5JUG74jgeGFgEVRwUvibrV5IwpYetucmJHVvOWcFxwoy5/n1JmVN2y0Gqo4HDg9unsiq9nEJt/ujJNM8qzxJu2Zt5iFyEgkAw3FlB3mNpQ4Pe1hKsc+8CP1/ERhOCMHVewbW6Clh7MeL07qcODfNU/j5Ott4pFliGm1R1d3FA8OXFTwXHjYEIRBwbBAe5WXe3KeNJMxL5ANZtUJz6C50g3zXI6lfmOJXBimFnSnXEGdOMyqB62tpFkzdw1QhzaV8sfEiMhU/TG1RATJGyCEWMVsXhhTm2HaepNq+30KrO24G3fIB8E9FbMyNlLMj+eEFSkpf/FAY7zPJ+xi02uJZSHgHAY+qhFpA3F8uNnCPhUMPaeOgU55OhyUUcvgUHy4+nun3ajvJQItUYREhO6U7C2Z/DlLgrKslcmLMwuGVDa0kq92mnspwHXlZiSSbTWQQkaOQSJ1trCSbnemNtDUWaAhW6jEQVbn8NVd3vJ4FKezgoIvAXhwKcpPbUvjj2EuL3fOElltB+wwu57V/45jZMSHvsWfi+vB2B42XIiU0y0lrb8oFFFLByBNCbiqfmkID9rm6TYM4zcf51izQr+F2zEy31G2WgpcZp8jDvKyqNihZVvfeis7HFt4mG6dXTL5r2ATVRrMsaJJEk7svJv5M802hlFvg5lEApKDdL6URubHc7iqcjA//xjjd6eCPSrEMswPP6TN2j9CBAvW4Qo64/c+9js22PV78ushOowkob4wCp90kKyZsELsYjP15oCYMkFBE8lsXC6i5bO/7BSGXDNbvVz4kV/hCOB3YsqwU2IF4/ME3ERDhM62zrNZeAyUf66BC6LGizxx/gxm9oSn2A3F24LUc1oHwrpW8FLIx3LU0vBsH173GpfO+3WSKjbq9nUXR+cym6DBlutsrtafrf1SK65dgZ55WIHx34Jwh5FEjXaE8h3f+b8HEok5lwKoO8cU6O+3ecdsaM=
BwIAAACkAABSU0EyAAgAAAEAAQCPuVnJ9eIt7iW/ocAMfJrrTaSnrcIfGmFHmkciEOpvDXFx+KSjXOwgWWVPn8Cs/1RoQYLESNw2rLGjAxxg42/GTC8QTYU8n50I3JokQVIWjrhEoL5czMBkMJTo/MQjO9u6F/OKShMBz5tQim1oLq8UFu3YcuGZpvdr3gfVWhQj1Yt7NceDPpr2cBZvP6nxEi9b2V8PLp1q8CfUdYUHabTkrO9A7mkszHFTqtzp7pwUmO4KvHGJU8nWkjqbmyy/Pgdt6w1xrLy8oacfrVxA2nTamY1l+HQSNv/g17sgjJs9w624rFaxGPuystJHddPMzKGx4tv4KR2RvNGV2wxm4OGhL1XfrBAyeAJa6mU/TtLPV1nxRB/66g7QA8i0m5YZd49RqhBhEG0Wx1g1iMWlBsnk4fiR593JSYJQc+/hcs8bQYO66eXL62vz00zdcGBjGJJQsEikQrgAigApinO588NuwPNuOyejomwJYPHlgqKh2qfgTYHVpXNV4XN7eW8ZReShieGyX5yJYBolkJ3Za9oAravyjvOS+dklwwZcENV1SEW6T2sI9PKe7sOzfCLR62gDHEWjAcsUVCacId4JEegVK9H6pbRjTQ8V5ecUHl/RqoTZ1eLeH55tdLEbCWk1K7RQZCwpmlKvSWd+jfIW5pa9qjBISXGyghyDiZdwaTWMtdkXqA/zhTd9/1hrmA5NKx0URx1gqJPySnIAPXoSzNdpjfCacLBTbkhn0pbcXPdhpT5lqWikImK6vgRNewf9Idkoe6vTL/YzmaYOe43WvXyyajMr4JUzxXR2t0QnWQVPOyQrgYwas/PLs1vdSmsZkhD+6Ni33wnbSJrk+hwmShUogcpvyiOLBb+jFYQFwlQbD1fxLgAmJu7Y1oWEUXf//ZLB0u2JA+H6hMBwAFs1i/4VA1OBNogFft7S3Iy6S1Gva7+2Ft+VjAsugcuZLcd+Fj1Y+9ff3Zx24Vbwo+g6Ngxv2iYUTm8Ek+LXuyXn1RQcbEckI/lkNUmBT1YkTcUcpoPozbWpvVbwv17oSnuckVSZLDJHpNbsNHvEEfVhlg7BjqH15+qUWttOX2uYJyN2aOwgFt5072KsW0ZHMh0pwewPW1bNdAdrDmGSu89KxB+Hbj2IFEAWIjrnHTFhE62lHpyb/6TfIzv1eFfZUEYkwznkBqcASHHuoO7y/oERyRbmHcFg1bs1HlyRRIiwY5RC7aN7b3ZnRr7AdbjZN0jFaJTZpNC28uDH2II1TlQ8fn7YlYQbS1a2Bvbz0FBb53nrUtrazZZHxE7M3DamtqTIWezL5X4YVcpP5M6NJ3lr3QzNgJgmbciuo0BmCSg6WK7vJo6XHHneoNahSIPiUB27NJa11IRrSSiK08dinkp4+HBu+5H/wmJfbwcfXGA9rudEivLCZcGKcx/FUwY+5nE6TqYPYw48YPVxc81r5td44AoEBhMc5SBHrIpyQpQb2T5jE+jLeClcMec53+6voaVTtT33TrLxBKAF+gP7EIBgzAeaGw2Jpm1R4w/ivtbe0zopLgA=
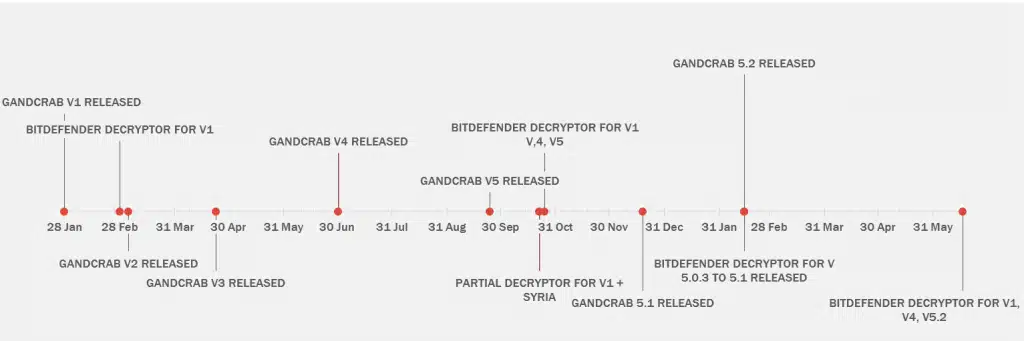
Below is he approximate chronology of GandCrab Ransomware versions (via BitDefender)
Another similar ransomware threat emerges
While the GandCrab actors claim their retirement, another ransomware strain has been gaining traction which looks strikingly similar. Dubbed “Sodinokibi”, the variant also has ID’s which correspond with specific files and Tor portal links to access from the ransom notes. This new ransomware variant utilizes existing MSP (Managed Service Provider) connections to execute installers on the endpoints. Inside the Tor portal, victims will find the same type of support and countdown timer which was once in the GandCrab portal. It is possible that the same distribution network from GandCrab might be deploying ransomware attacks with these new vectors.
How to protect your data from ransomware
It’s now more important than ever before to protect your data from cyber threats such as ransomware:
Create regular, offsite backups
One of the strongest ransomware prevention procedures is to backup your organization’s data to an external source. Create backups both online (in the cloud) and also on physical storage devices that can be accessed offline and kept in a secure location. With a regular backup schedule, your business will have all the data protected in case there is a ransomware incident. Do NOT keep backups of data on the same local drive, as these can become encrypted when the ransomware runs the encryption programming.
Implement endpoint protection
Stop the ransomware variant before it spreads by utilizing quality security endpoint solutions on company network systems. Software such as Malwarebytes or Sophos can be accessible (and affordable) for many organizations making this a cost-effective way to reduce ransomware risk and close vulnerabilities. These endpoints help detect incoming threats, such as ransomware, that try and execute malicious code on the network. Attacks come through open RDP (Remote Desktop Protocol) ports that enable unauthorized, outside users to make major access changes and infiltrate the network. Closing these RDP ports can greatly reduce risks for ransomware attacks.
Consult with a security specialist
Depending on your industry, company size, and IT needs, there might be certain security exposures that require special attention. It’s wise to consult with a trained security expert to have a more defined approach in which all security policies & procedures are taken into account and the appropriate solutions are implemented. The best solution to a ransomware attack is having proper safeguards in place before data is encrypted, which requires proactiveness and awareness early on.
Want to know how much cyber security costs?
Our cyber security costs guide will help you learn about the expenses for protecting your business!
Cyber Security Costs Guide