Ransomware prevention is critical for businesses in any industry to protect their data from being encrypted by ransomware. Companies and individuals can protect their data using cybersecurity solutions, such as software or services that help to prevent threats, detect ransomware, and recover from cyberattacks.
These solutions work by detecting suspicious activities that could indicate a ransomware attack, such as changes to system files or unusual network traffic. Once detected, the ransomware protection software will either stop the attack or limit the damage caused by isolating the infected system, preventing the ransomware from spreading to other devices.
Ransomware mitigation solutions
Preventing ransomware is the best security solution you can provide your business with. However, if your prevention solutions fail, immediate actions can mitigate the damage and help your business survive after the attack.
Ransomware mitigation involves responding effectively once an attack has occurred, limiting its impact, and facilitating recovery.
Key ransomware mitigation strategies:
Advanced threat detection through real-time monitoring
Advanced real-time monitoring has become crucial in detecting and preventing ransomware attacks before they cause significant damage. Security Information and Event Management (SIEM) systems play a pivotal role by aggregating and analyzing security data from multiple sources across an organization’s network.

Modern monitoring solutions leverage machine learning (ML) and artificial intelligence (AI) to identify suspicious patterns and potential threats that traditional rule-based systems might miss. These technologies can detect anomalies in network traffic, user behavior, and system activities that could indicate a potential ransomware attack.
Build a resilient data backup strategy
A robust backup strategy is the most critical defense against ransomware. The 3-2-1 backup rule remains a gold standard: maintaining three copies of data on two different media types, with at least one copy stored off-site or offline.
Regular backup testing is crucial to ensure data can be successfully restored in an emergency. Cloud-based backup solutions now offer additional layers of protection, with advanced encryption and geographical redundancy that protect against both cyber threats and physical infrastructure failures.

Implement network segmentation for cyber isolation
Network segmentation divides the network into smaller, isolating segments, allowing organizations to prevent ransomware from quickly propagating across entire systems.
Each segment can have its own security controls, access permissions, and monitoring, effectively creating digital firewalls that contain potential breaches.
Enhance security with multi-factor authentication
MFA requires users to provide multiple verification forms before accessing systems, significantly reducing the risk of unauthorized access through stolen credentials. This strategy goes beyond traditional password protection, incorporating elements like biometric verification, hardware tokens, or mobile authentication apps.
Empower employees through cybersecurity education
Comprehensive and ongoing security awareness training is essential in preventing ransomware attacks. This includes educating employees about phishing techniques, social engineering tactics, and best practices for digital security.
Training should be dynamic, incorporating:
- Real-world examples
- Simulated phishing exercises
- Up-to-date information about emerging threats
Maintain system integrity through timely updates
Cyber threat actors know that many people allow their security systems to function without timely updates, which makes the systems vulnerable to exploitation.
Enabling automatic updates is the easiest way to ensure software updates/patches. If this protocol is enabled, do not respond to any communication offering the ‘update,’ as malware authors often send these notifications.
Enable hidden file extensions
Ransomware has been successful due to its sneaky ability to hide damaging .exe files within seemingly harmless files such as PDFs. This ability is a loophole within the Windows environment as it allows hidden files.
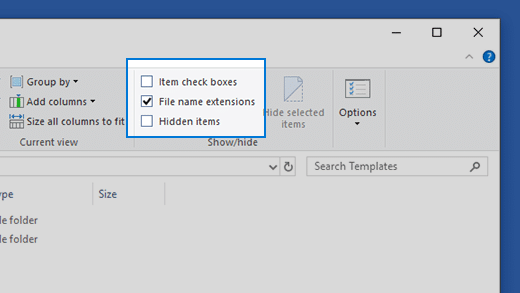
To enable hidden files extension on Windows 8 and 10:
- Open File Explorer
- Click the View tab
- Select “File name extension”
- Optionally, you can enable Hidden items
- Filename extensions will now be visible
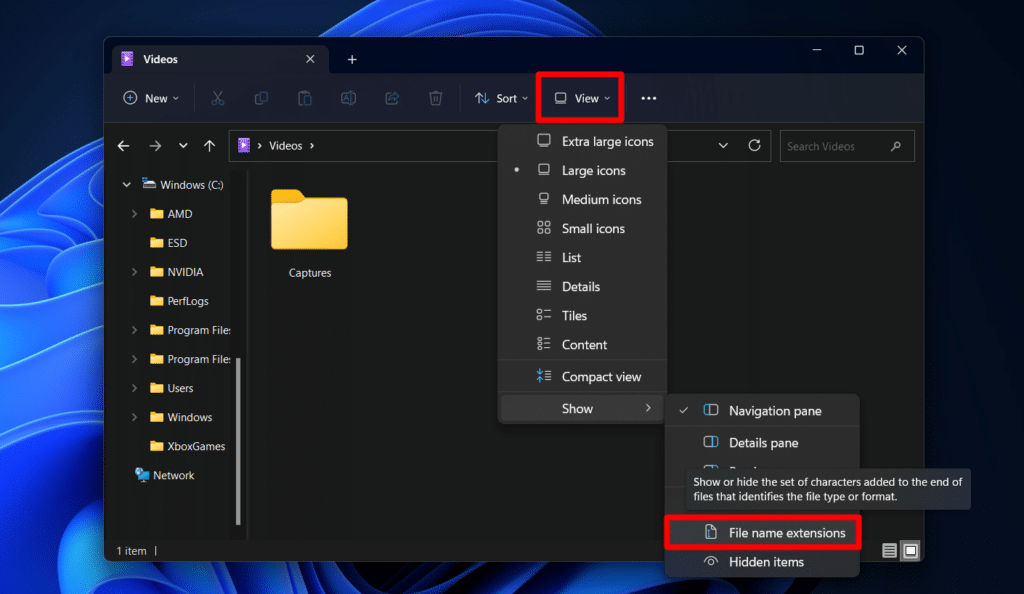
To show the file extension on Windows 11
- Open File Explorer
- Go to View > Show > File Name Extensions
Create strong passwords
Proven Data has encountered a surprisingly large number of ransomware recovery cases due to weak username and password combinations. Hackers have tools to scan and brute-force weak passwords quite easily. To avoid this, cybersecurity experts recommend using a strong password generator and never repeating passwords.
What should you do if you have been affected by a ransomware attack?
If you have been the victim of a ransomware attack, you have limited options. Ransomware recovery and removal services can help limit the damage.
Also, remember that ransomware costs to your business go beyond the recovery, as the recovery time leads to prolonged downtime that prevents your business from working.
1. Immediately disconnect the network
If you suspect a ransomware attack, time is of the essence, as the encryption process is fast to complete the encryption process. Disconnect the infected machine from the network servers to prevent the malware from spreading. This is not a guarantee against encryption but will limit the damage.
2. Contact authorities
Since cyberattacks are a crime, you must report the ransomware to local authorities. In the USA, the responsible entity for cybercrime investigation is the FBI.
You should provide every detail about the attack you have to assist with the investigation. The best way to do so is to create a digital forensic report.
3. Use your system-restore/shadow copies to return to a previous condition
If you are using Windows and have the System Restore enabled, you can use this to return to an earlier state before ransomware encryption.
Remember that most ransomware is programmed to delete shadow copies to prevent users from restoring the data.
4. Contact a ransomware removal service provider
Contact a ransomware removal service to eliminate any trace of the ransomware, close backdoors hackers can use to make a new attack, and restore encrypted data.