Early in December, the United States Treasury Department Office of Foreign Assets Control (OFAC) released new sanctions against the Russian cyber criminal gang Evil Corp that is responsible for the Dridex malware.
Who is Evil Corp?
The detailed report from the U.S. Treasury Department delivers sanctions around the cybercriminal gang Evil Corp and it’s members. Operating as a business structure out of Moscow, Russia, the group has successfully accumulated at least $100 million through illicit cyber activities & extortion campaigns. Their leader, Maksim “Aqua” Yakubets has been added to the FBI Most Wanted list alongside various charges including conspiracy, conspiracy to commit fraud, wire fraud, bank fraud, and intentional damage to a computer. Yakubets was also charged in connection with ‘Zeus’ malware that affected tens of thousands of computers & networks in the United States.
Sanctions against Evil Corp
On December 5th, 2019, as a result of the findings around Dridex and Evil Corp, the U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) is officially taking action against the cyber gang and their illicit activities. The sanctions are the result of a coordinated investigation with the United Kingdom’s National Crime Agency (NCA), the Treasury Department Financial Crimes Enforcement Network (FinCEN), and the Treasury Department’s Office of Cybersecurity and Critical Infrastructure Protection (OCCIP).
Also charged in connection with Evil Corp is Denis Gusev (Gusev) who serves as a senior member in the cyber gang. Since 2017, Gusev has been investigated upon and found to be assisting Evil Corp in providing new office space and business connections for the cybercriminal organization. Biznes-Stolitsa, OOO, Optima, OOO, Treid-Invest, OOO, TSAO, OOO, Vertikal, OOO, and Yunikom, OOO are the Russian business entities associated with the cyber criminal activity of Evil Corp. Additional Russian citizens with Evil Corp have been found in pursuant of the U.S. Treasury Department’s Executive Order 13694 which outlaws “significant malicious cyber-enabled activities”.
Dridex malware
Having first appeared in 2012, Dridex is the name of the malware used by Evil Corp to harvest credentials, data, and perform surveillance on a victim’s computer & network system. The CISA Alert (AA19-339A) indicates that this malware is often used as a tool to leverage criminal activity for use against the banking & financial industries. In a report from the U.S. Department of the Treasury, Evil Corp has targeted nearly 300 financial institutions and banks in over 40 countries around the world. Many of their victims are banks located within the United States and the United Kingdom.
How it works
Since its beginning in 2012, the cyber security community has seen many different variants and implementations of the Dridex malware and its ability to adapt to new browser patchwork over the years. The malware relies on unsuspecting users to load an entire module that hosts a folder of exploitation and executable software. Dridex also heavily exploits vulnerability CVE-2017-0199 that permits remote execution of code in Microsoft’s WordPad and Office platforms.
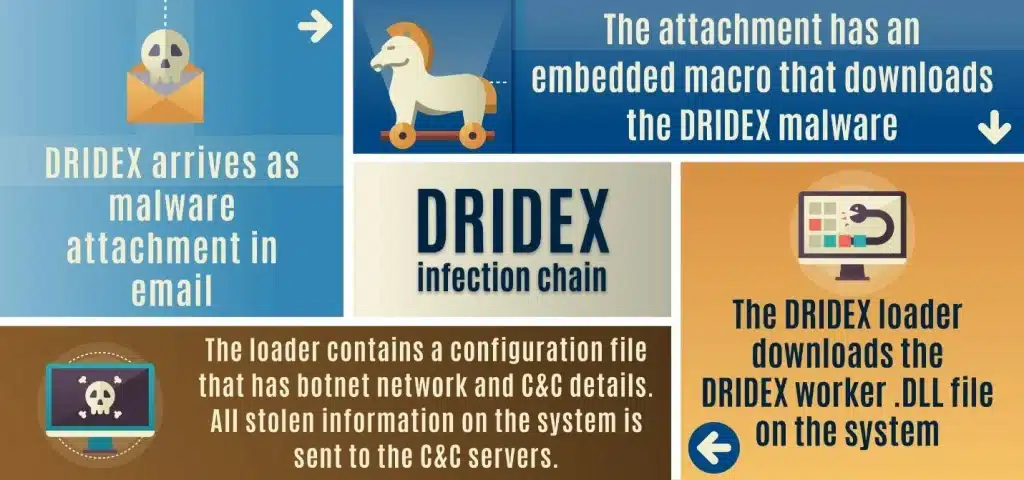
How is it distributed?
A large part of the Dridex malware success can be attributed to Evil Corp’s ability to build large-scale phishing campaigns. Using better syntax & research of victims, the cyber criminal gang is able to craft more convincing email campaigns that are sent to victims. Evil Corp members have been found to “employ a combination of legitimate business names and domains, professional terminology, and language implying urgency to persuade victims to activate open attachments” according to the US Cybersecurity Infrastructure Agency.
Ransomware operators
Dridex has gone through several modifications, in which the malware variant is adapted to focus on encryption-based cyber crimes such as ransomware. Security researchers have found similarities between Dridex and BitPaymer (Friedex), as both use the same code structure and deployment methods. The United States’ Cybersecurity and Infrastructure Security Agency also revealed similarities between Locky ransomware and it’s variants Zepto and Osiris. These ransomware variants are loaded using the same vulnerabilities exploited alongside Dridex.
How to protect your data from malware
After learning how malware can impact your organization, we recommend taking proactive steps to ensure you’re protected:
Train your employees
Malware such as Dridex & BitPaymer enters the network most commonly through large phishing email campaigns. These campaigns rely on unsuspecting employees to click on links & download executables that are unauthorized. Having regular training sessions around cyber security and malware/ransomware can encourage employees to look more closely and the data they send & receive which can greatly reduce the risk of a cyber attack.
Keep software/hardware updated
Dridex thrives when businesses forget to update their software & hardware configurations across the network. The malware uses vulnerabilities in patchwork to exploit privileges and features that are then later closed in further manufacturer updates. For example, Dridex was able to execute a “loader” module on victim’s computers that used an older version on Microsoft Office and WordPad. The patch to close this vulnerability was released in 2017, and these updates should be mandated through procedures in which keeps all software & hardware to the latest updated patch.
Track privileges and user activity
Cyber criminals thrive in network environments that have little to no privileged access management (PAM). It’s recommended to keep a log of which users have elevated access to change network & administrative settings. Threat actors will often target users with higher levels of access so that they can change permissions settings and create an advantage in the level of control over the business. Organizations can also follow the National Security Agency’s ‘Top Ten Cybersecurity Mitigation Strategies’ which outlines actions businesses can take to prevent becoming a victim of a cyber crime.
Reporting cyber crime
Authorities are able to apply these sanctions due to collective data & reports on cyber crime across the nation and the world. Reporting a cyber crime can help law enforcement track down and detect cyber criminal activity, giving the public a better advantage to understanding these cyber gangs and illicit activity.
If you are a victim of a cyber crime, reporting ransomware to authorities is the utmost importance.
We have provided a world wide reference on where to report these cyber crimes based on your location.
Through the collaboration of local, state, federal & global cyber crime agencies, these legal developments and sanctions have sent a strong message for the consequences of cyber-related criminal activity and extortion around the globe. However, this also presents a positive opportunity for businesses to be proactive in their cyber security defenses and take these cyber threats seriously.