Medusa ransomware, which is not the same as MedusaLocker, made its debut in June 2021 and has since become a prominent threat in the realm of cybersecurity. Medusa ransomware operates as a Ransomware-as-a-Service (RaaS) model, collaborating with global affiliates to enhance its impact.
In this comprehensive article, we will explore the Medusa ransomware variant in detail, and provide information on the indicators of compromise (IOC) associated with the group’s activity. It’s essential to understand which industries the ransomware targets and have some insight into how it operates to improve your cybersecurity and ransomware defense.
Medusa ransomware overview
Characterized by multifaceted attacks, each encrypted by Medusa ransomware file bears diverse extensions, with “.MEDUSA” being a distinctive mark. The ransomware exhibits numerous variants, as illustrated by a range of file extensions.
Medusa’s attack strategy involves exploiting vulnerable Remote Desktop Protocols (RDP) and deceptive phishing campaigns. Employing PowerShell for command execution, it systematically erases shadow copy backups, hindering data restoration.
Medusa TOR website serves as a platform for victim announcements, providing contact information and evidence of stolen data. The attackers predominantly target North and South America and Europe, with the United States and the United Kingdom being prime targets.
How to identify Medusa ransomware: Main IOCs
Indicators of compromise (IOCs) are pieces of forensic data that can help identify malicious activity or malware associated with a cyber attack. It includes the encryption extension, file hashes, and IP addresses, among other details cyber criminals leave as they infect a machine or system.
But, if you can’t identify the ransomware strain through its IOCs, you can use Proven Data’s free ransomware ID tool to check if the Medusa ransomware is the malware that encrypts your files.
Important: Some of these indicators require technical knowledge of the infected system, so you may need to contact your IT team or a digital forensics service provider.
Medusa ransomware-specific IOCs include:
Encrypted Files Extension
- .MEDUSA
Ransom Demanding Message
- !!!READ_ME_MEDUSA!!!.txt
Detection Names
- Avast Win32:RansomX-gen [Ransom]
- Emsisoft Gen:Heur.Ransom.REntS.Gen.1 (B)
- Kaspersky Trojan.Win32.AntiAV.dadw
- Malwarebytes Ransom.Medusa
- Sophos Mal/Generic-S
Medusa Tor negotiation site
- medusacegu2ufmc3kx2kkqicrlcxdettsjcenhjena6uannk5f4ffuyd[.]onion
How Medusa ransomware works
Medusa follows an attack method to both encrypt and steal data from victims. This tactic is known as double extortion since the threat actors demand payment for both the decryption key and to do not release the stolen data on their TOR website.
Initial Access
Medusa ransomware gains initial access through the exploitation of vulnerable services, often targeting public-facing assets or applications with known unpatched vulnerabilities.
Legitimate accounts are hijacked, and initial access brokers may be utilized for infiltration. In one observed incident, a webshell was uploaded to an exploited Microsoft Exchange Server.
Propagation and Defense Evasion
Medusa ransomware propagates through a variety of means, including the deployment of webshells, PowerShell scripts, and exploiting vulnerable services.
To avoid detection, Medusa operators drop kernel drivers guarded by a software protector called Safengine Shielden. The ransomware uses packed loaders with fake UPX headers and employs obfuscation techniques to obscure its code flow.
Two drivers are dropped, each targeting specific security endpoint products for termination or deletion.
Discovery and Reconnaissance
Medusa operators use tools like SoftPerfect Network Scanner for remote service discovery, including options for WMI, Registry, Services, Files, SNMP, SSH, and PowerShell.
Remote scripts, often in Cyrillic script, are used for reconnaissance and information gathering on compromised systems.
Ransomware Execution
The ransomware binary, referred to as “Gaze,” is executed with various parameters, allowing it to check its version, use network drives, exclude certain folders, avoid self-deletion, and more.
String encryption is employed for targeted services, processes, file extensions, and folder paths.
File Encryption
Medusa uses RSA asymmetric encryption to protect the AES256 key used for encrypting victims’ files. Encrypted files are renamed with the “.medusa” extension.
Certain files and folders are excluded from encryption to ensure the system remains functional.
Ransom Note and Communication
A ransom note, typically named !!!READ_ME_MEDUSA!!!.txt is dropped, containing information about the attack, guarantees, contact details, and instructions for using TOR.
Important: Do not pay the ransom. Paying the ransom does not guarantee that you will get your data back, and it may encourage the attackers to continue their criminal activities. Check our in-depth article on what happens if you pay the ransom.
How to handle a Medusa ransomware attack
It is important to note that handling a ransomware attack can be complex and requires expertise. Therefore, it is recommended to seek professional help from a reputable data recovery service, such as Proven Data to help you recover your data and remove the ransomware from your system.
You can also report the attack to law enforcement agencies, such as the FBI, and cybersecurity organizations to help prevent future attacks and catch the perpetrators.
We strongly recommend contacting cybersecurity services to handle ransomware attacks. Proven Data technicians not only retrieve ransomware-encrypted data but also create forensic reports and streamline incident response, minimizing your business downtime and financial loss.
Notable attacks by Medusa ransomware
The notorious Medusa ransomware gang has recently orchestrated a series of high-profile cyberattacks, targeting diverse entities such as Toyota Financial Services (TFS), the Minneapolis Public School (MPS) District, and the Philippine Health Insurance Corporation (PhilHealth). These attacks not only disrupted operations but also exposed sensitive data, highlighting the evolving and audacious tactics of cybercriminals.
1. Toyota Financial Services (TFS) Breach
On November 16, 2023, TFS, a global subsidiary of Toyota Motor Corporation, confirmed unauthorized access to its systems in Europe and Africa following a Medusa ransomware claim. Security analysts highlighted a potential vulnerability in TFS’s German office related to an unpatched Citrix Gateway endpoint, indicating a risk of exploitation.
Toyota confirmed the threat group demanded an $8 million ransom and threatened to leak allegedly stolen data. The ransom note gave Toyota a 10-day ultimatum, with an extension option for $10,000 per day.
To substantiate their intrusion, the hackers published sample data encompassing financial documents, spreadsheets, hashed account passwords, internal organization charts, and more.
2. Minneapolis Public School (MPS) District Attack
In February of 2023, Medusa not only encrypted data but also exfiltrated around 100 GB of sensitive information of the Minneapolis Public School (MPS) District. The group later published this data on the internet, including highly confidential student and faculty details. MPS resisted Medusa’s $1 million ransom demand, claiming to have successfully restored encrypted systems via backups.
Medusa chose to publish the stolen data on a conventional website rather than the typical dark web leak site. Social media amplification heightened the exposure of the information.
3. Philippine Health Insurance Corporation (PhilHealth)
On September 22, 2023, Medusa stole almost 750 gigabytes of information, including sensitive data from millions of PhilHealth members. The group made the stolen data available on the dark web, issuing a ransom demand of around $300,000.
PhilHealth confirmed being unprotected by antivirus software during the Medusa ransomware attack. The antivirus had expired, and renewal was delayed due to government procurement processes.
PhilHealth managed to recover its systems swiftly after the attack, restoring public-facing applications by October 6, 2023.
How to prevent Medusa ransomware attacks
Preventing Medusa ransomware attacks is always the best cybersecurity tactic. If you are a recent victim, you must follow these tips to avoid a new ransomware attack:
Keep your software up to date
Regularly update your operating system and programs to uphold security standards. Reputable OS providers will consistently check their software for vulnerabilities and patch up their security standards to protect against newly detected threats.
Use reputable antivirus software
Employ reputable antivirus software to bolster protection against malware significantly, and regularly check that it is updated. You can also check your network for vulnerabilities and learn where you need to improve your security system.
Be cautious of suspicious emails
Even though there are no known cases of Medusa using phishing as an attack method, it’s important to exercise caution when dealing with emails from unfamiliar or dubious origins. Refrain from opening files or clicking on links within emails that you are not expecting or seem suspicious.
Do not download cracked software
Cracked software is the term used to describe illicitly modified or pirated versions of commercial software, typically distributed without proper authorization or licensing. Cybercriminals frequently conceal their ransomware executables within cracked software distribution websites, leading users to unwittingly download and execute the malware.
Backup your data
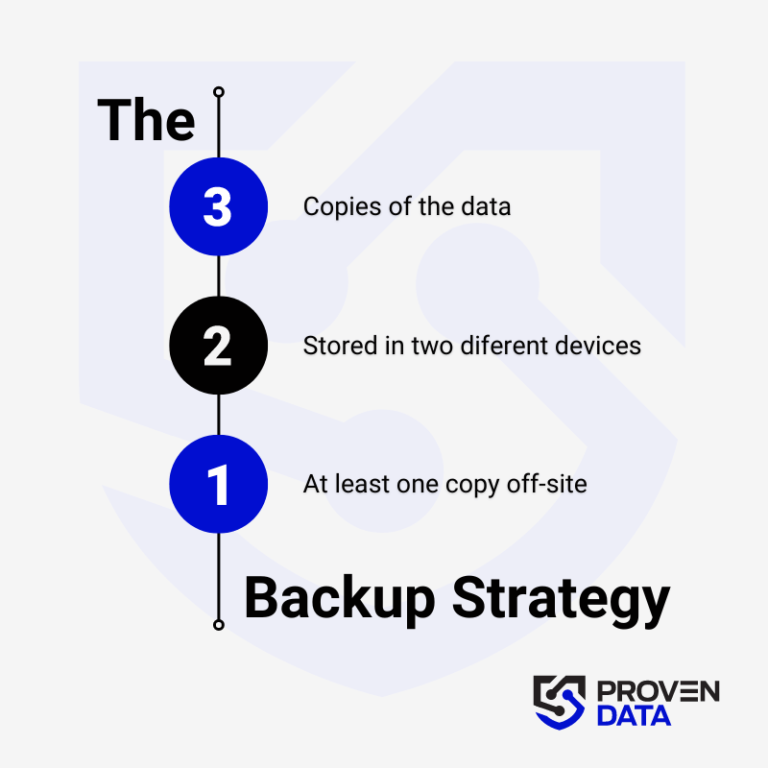
Regularly back up your data to an external hard drive or cloud storage service to prevent complete data loss in case of a ransomware attack. A highly recommended strategy for data loss prevention is the 3-2-1 backup strategy.
The 3-2-1 backup strategy involves creating three total copies of your data: two on different media and one offsite, ensuring redundancy and protection against data loss. And at least one copy offsite to prevent loss due to natural disasters or other local incidents.
Educate yourself and your teams
Educate yourself and your employees about the risks of ransomware and how to avoid it, such as avoiding suspicious emails or downloads.
Consult cybersecurity professionals
Proven Data offers cyber security services to help you keep your data protected against threat actors. From vulnerability assessment to ensure your systems and servers do not have open doors for cyber attacks, to Incident Response (IR) services for immediate response in case of a successful attack.
We also have the option of managed detection and response (MDR) services that help organizations improve their security posture, minimize risk, and protect sensitive data and assets.