This rising digital threat has swiftly gained notoriety for its sophisticated tactics and unique operational approach. Akira ransomware stands out with its distinctive payment options and double extortion techniques. As Akira continues to evolve, monitoring and understanding its tactics are crucial for cybersecurity efforts.
In this comprehensive article, we will explore the Akira ransomware group techniques, how the attack happens, and what to do if Akira compromises your systems or machines. Also, see how you can protect your business’s sensitive and critical data by taking simple preventive actions.
Akira ransomware overview
Akira ransomware quickly gained fame for its advanced tactics since its debut in March 2023. It operates through a Ransomware-as-a-Service (RaaS) model, featuring distinctive payment choices and double extortion methods.
The Tor leak site has a retro 1980s aesthetic, providing a visually striking contrast to the high-stakes digital landscape it dominates.
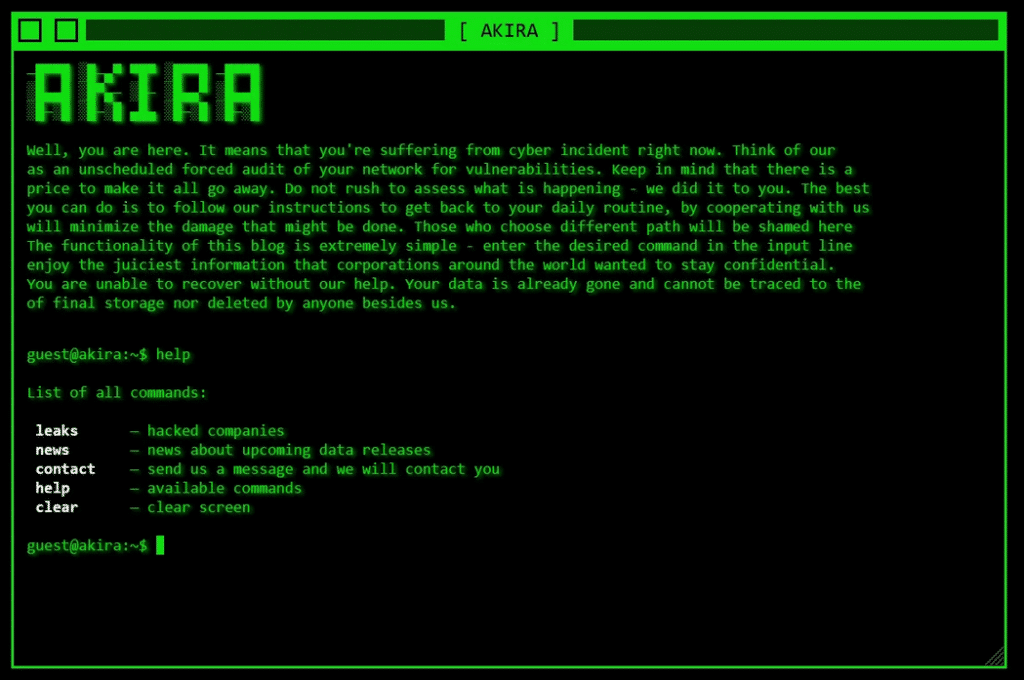
Even though it has the same name as an older version from 2017, Akira has its own style, being a completely new cyberthreat gang. The people behind Akira, linked to the Conti gang, give victims a choice – either pay to unlock files or pay to delete their stolen data. They’re flexible and financially motivated, asking for anywhere between $200,000 to a massive $4 million.
The ransomware’s reach extends beyond conventional targets, as evidenced by its expansion into Linux machines. They also exploit a zero-day vulnerability in Cisco ASA and FTD software (CVE-2023-20269).
How to identify Akira ransomware: Main IOCs
Indicators of compromise (IOCs) are pieces of forensic data that can help identify malicious activity or malware associated with a cyber attack. It includes the encryption extension, file hashes, and IP addresses, among other details cyber criminals leave as they infect a machine or system.
But, if you can’t identify the ransomware strain through its IOCs, you can use Proven Data’s free ransomware ID tool to check if the Akira ransomware is the one that encrypts your files.
Important: Some of these indicators require technical knowledge of the infected system, so you may need to contact your IT team or a digital forensics service provider.
Akira ransomware IOCs include:
SHA-256, Secure Hash Algorithm 256-bit, is a cryptographic hash function that belongs to the SHA-2 family of hash functions. It’s designed to take an input message and produce a fixed-size output hash value of 256 bits (or 64 hexadecimal characters).
A hash is a function that takes an input (or ‘message’) and produces a fixed-size string of characters, which is typically a hexadecimal number. The output, known as the hash value or hash code, is unique to the input data.
SHA-256 is widely used in various security applications and protocols, including digital signatures, certificate generation, and integrity verification.
Windows versions of SHA-256 hash files
- 3c92bfc71004340ebc00146ced294bc94f49f6a5e212016ac05e7d10fcb3312c
- 5c62626731856fb5e669473b39ac3deb0052b32981863f8cf697ae01c80512e5
- 678ec8734367c7547794a604cc65e74a0f42320d85a6dce20c214e3b4536bb33
- 7b295a10d54c870d59fab3a83a8b983282f6250a0be9df581334eb93d53f3488
- 8631ac37f605daacf47095955837ec5abbd5e98c540ffd58bb9bf873b1685a50
- 1b6af2fbbc636180dd7bae825486ccc45e42aefbb304d5f83fafca4d637c13cc
- 9ca333b2e88ab35f608e447b0e3b821a6e04c4b0c76545177890fb16adcab163
- d0510e1d89640c9650782e882fe3b9afba00303b126ec38fdc5f1c1484341959
- 6cadab96185dbe6f3a7b95cf2f97d6ac395785607baa6ed7bf363deeb59cc360
Linux version of SHA-256 hash file
- 1d3b5c650533d13c81e325972a912e3ff8776e36e18bca966dae50735f8ab296
How Akira ransomware works
Akira ransomware, a formidable digital adversary, orchestrates a multifaceted intrusion marked by sophisticated tactics and strategic exploitation. This overview delves into the step-by-step workings of Akira ransomware, unraveling its modus operandi from initial access to the impactful encryption of targeted systems.
Initial Access
Akira ransomware initiates its intrusion through diverse methods, frequently exploiting compromised Virtual Private Network (VPN) credentials. Notably, it specifically targets vulnerable systems, with a keen focus on Cisco VPNs. Exploiting distinct vulnerabilities, such as the zero-day CVE-2023-20269 in Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) software, the ransomware gains an initial foothold in the victim’s environment.
Persistence
Upon infiltrating a system, Akira ensures its continued presence and control by establishing persistence. This involves the creation of a new domain account within the compromised system. By doing so, the ransomware guarantees ongoing access, allowing it to operate stealthily and execute its malicious activities without detection.
Defense Evasion
To thwart detection and impede security measures, Akira employs advanced tools like PowerTool or a KillAV tool. Leveraging the Zemana AntiMalware driver, it terminates processes related to antivirus software. This evasion tactic is crucial for the ransomware to operate undetected and maximize the impact of its malicious activities.
Discovery
Akira’s operators engage in thorough reconnaissance using a suite of tools. PCHunter and SharpHound are utilized to gather detailed system information. Additionally, AdFind, along with net Windows commands, extracts valuable domain information. Advanced IP Scanner and MASSCAN play a key role in identifying other remote systems connected to the victim’s network.
Lateral Movement
To enhance its lateral movement within the victim’s network, Akira ransomware employs tools like Mimikatz, LaZagne, or specific command lines.
These tools are instrumental in extracting credentials, providing the ransomware with the necessary access to move laterally and escalate its impact within the compromised environment.
This strategic approach allows Akira to spread seamlessly within the victim’s infrastructure, broadening its reach and intensifying the scope of its ransomware activities.
Command and Control
Akira ensures control and facilitates the exfiltration of stolen information through the utilization of third-party tools and web services. Tools like RClone, AnyDesk, Radmin, Cloudflare Tunnel, MobaXterm, RustDesk, and Ngrok are employed to establish command and control, enabling the ransomware to operate effectively and exfiltrate sensitive data.
Exfiltration
The exfiltration of stolen information is orchestrated using RClone, a third-party tool and web service. Additionally, Akira may leverage FileZilla or WinSCP for transferring data via File Transfer Protocol (FTP). This systematic approach allows the ransomware to discreetly remove sensitive information from the compromised environment.
Encryption
Akira employs a sophisticated hybrid encryption algorithm, combining Chacha20 and RSA, to encrypt targeted systems effectively. It adapts its encryption methods based on the file type and size, supporting full, partial, and spot encryption modes.
Impact
Upon successful encryption, Akira appends the “.akira” extension to encrypted files, impeding system recovery by deleting shadow copies. It strategically targets specific directories while avoiding the encryption of predefined file types and extensions.
Important: Do not pay the ransom. Paying the ransom does not guarantee that you will get your data back, and it may encourage the attackers to continue their criminal activities. Check our in-depth article on what happens if you pay the ransom.
How to handle an Akira ransomware attack
It is important to note that handling a ransomware attack can be complex and requires expertise. Therefore, it is recommended to seek professional help from a reputable data recovery service, such as Proven Data to help you recover your data and remove the ransomware from your system.
You can also report the attack to law enforcement agencies, such as the FBI, and cybersecurity organizations to help prevent future attacks and catch the perpetrators.
We strongly recommend contacting cybersecurity services to handle ransomware attacks. Proven Data technicians not only retrieve ransomware-encrypted data but also create forensic reports and streamline incident response, minimizing your business downtime and financial loss.
How to prevent ransomware attacks
Preventing Akira ransomware attacks is always the best cybersecurity tactic. If you are a recent victim, you must follow these tips to avoid a new ransomware attack:
Keep your software up to date
Regularly update your operating system and programs to uphold security standards. Reputable OS providers will consistently check their software for vulnerabilities and patch up their security standards to protect against newly detected threats.
Use reputable antivirus software
Employ reputable antivirus software to significantly bolster protection against malware, and regularly check that it is updated. You can also check your network for vulnerabilities and learn where you need to improve your security system.
Be cautious of suspicious emails
Since phishing emails are one of the most common attack methods used by cybercriminals, it’s critical to exercise caution when dealing with emails from unfamiliar or dubious origins. Refrain from opening files or clicking on links within emails that you are not expecting or that seem suspicious.
Do not download cracked software
Cracked software is the term used to describe illicitly modified or pirated versions of commercial software, typically distributed without proper authorization or licensing. Cybercriminals frequently conceal their ransomware executables within cracked software distribution websites, leading users to unintentionally download and execute the malware.
Backup your data
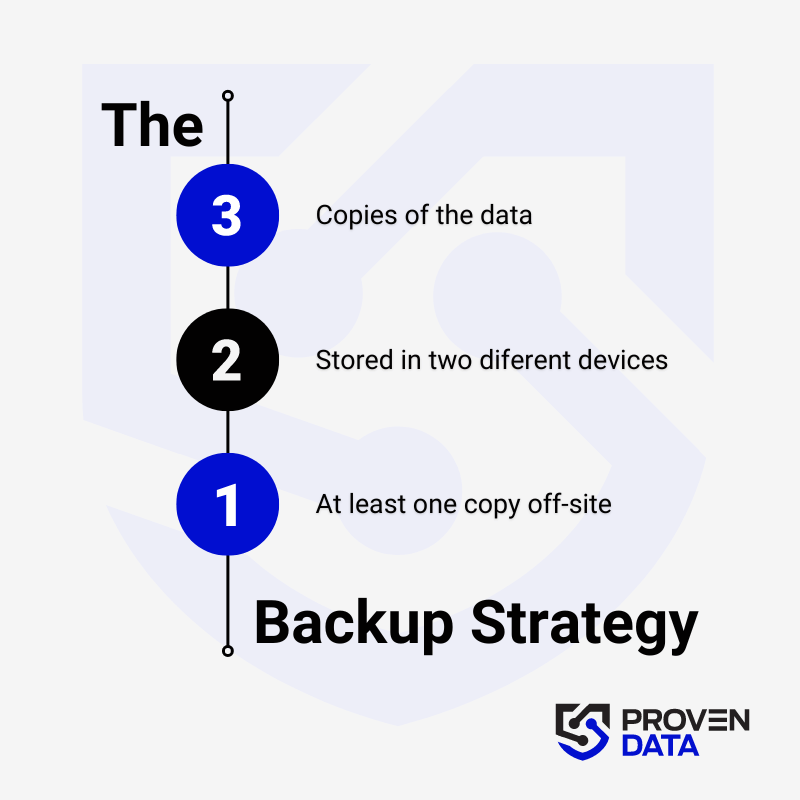
Regularly back up your data to an external hard drive or cloud storage service to prevent complete data loss in case of a ransomware attack. A highly recommended strategy for data loss prevention is the 3-2-1 backup strategy.
The 3-2-1 backup strategy involves creating three total copies of your data: two on different media and one offsite, ensuring redundancy and protection against data loss.
Educate yourself and your teams
Educate yourself and your employees about the risks of ransomware and how to avoid it, such as avoiding suspicious emails or downloads.
Trust cybersecurity professionals
Proven Data offers cyber security services to help you keep your data protected against threat actors. From vulnerability assessment to ensure your systems and servers do not have open doors for cyber attacks, to Incident Response (IR) services for immediate response in case of a successful attack.
We also have the option of managed detection and response (MDR) services that help organizations improve their security posture, minimize risk, and protect sensitive data and assets.