You’ve been hit by a ransomware attack and need to know how to recover. You’ve done some research and discovered that there are companies offering ransomware recovery services. What exactly are ransomware recovery services and do you need one?
We are here to help you sort out what ransomware recovery option is right for you. At Proven Data, we’ve recovered data and secured networks from thousands of previous clients impacted by ransomware around the world.
Naturally, we’re a bit biased when it comes to the benefits or ransomware recovery services. That’s why in this article, you will find a detailed breakdown of just exactly what we see as so beneficial about ransomware recovery services.
Don’t take our word for it; keep reading and decide for yourself if working with a ransomware recovery service is right for you.
By the end of this article, you will:
- Know the benefits of using ransomware recovery services to restore your data
- Find answers to the common concerns about ransomware recovery
What do ransomware recovery services do?
When you are hit with a ransomware attack, you need to know how to remediate, recover, and prevent future attacks. Regardless of what method you choose to recover from a ransomware attack, you need to ensure that your business fully recovers from the attack and is resilient to future cyber incidents.
Below, you will find the top 8 most valuable aspects of a ransomware recovery service that will help you successfully navigate ransomware recovery.
1. Guaranteed ransomware virus removal
Whether you can restore your data from backups or you pay for a decryption key, it is critical to remove the ransomware virus from your infected devices.
Removing the ransomware virus will not decrypt your files, but it is a crucial step to securing the environment from active threats and back doors.
This is one of the most important elements of a recovery service. Why? Here is a real life scenario:
Company A pays the ransom, receives a decryption key, decrypts their files and their business returns back to normal after a few days. Flash forward 1 month, the hacker comes back as a result of a backdoor that was left open and encrypts the entire network again with a brand new key.
Repeat ransomware attacks occur more often than you would expect. A ransomware recovery company who regularly deals with a specific ransomware strain will use prior threat intelligence to guide you in cleaning your environment and patching security vulnerabilities.
A ransomware recovery service can provide guaranteed ransomware removal to ensure all backdoors are closed and your network is safe to resume business operations. For this reason alone, it is highly recommended to go with an experienced ransomware recovery service.
2. Explore every available ransomware recovery option
When researching ransomware recovery methods, your top priority is to get your data back and your business up and running as soon as possible.
Unfortunately, many ransomware encryptions are too sophisticated and strong to be broken by any method other than paying the ransom.
However, you should never pay the ransom without exploring all possible recovery methods for the specific variant that has infected your network.
But how do you know where to start researching ransomware recovery options? A ransomware recovery service can help.
By choosing to work with ransomware recovery professionals, you will have access to experts who have worked with thousands of ransomware incidents and different variants.
The knowledge and tools that professional ransomware recovery experts have can assure you that every option is explored to recover your files.
Other options outside of the ransom include:
- Repairing or extracting data from partially encrypted databases or virtual images.
- Using undelete software.
- Restoration from shadow copies.
- Exploring if the encryption can be broken.
3. Leverage threat intelligence on previous ransomware actors
You’ve discovered there are no other options left other than to pay the ransom. You are ready to pay the demanded amount to unlock your files, so why do you need to pay a ransomware recovery service to assist you in decrypting your files? How complicated can it be?
While paying a ransom in exchange for a decryption key might seem straightforward, engaging with the cyber criminal always poses risks.
A ransomware recovery service can use threat intelligence from prior experience to help you make informed decisions. Useful information includes:
- The probability the threat actor will deliver a key after the ransom is paid
- The probability the threat actor will ask for a second payment after the ransom is paid
- The recovery rate of files for the specific ransomware variant
- The average initial ransom demand
- The average negotiated ransom demand
- Whether the decryption tool tends to be faulty for the specific ransomware variant
- Whether the ransomware group is known to remove data from your network
- Typical attack vectors used and vulnerabilities exploited for your specific ransomware variant
Using threat intelligence from prior ransomware incidents, the ransomware recovery service can guide you through the recovery process with these data analytics.
4. Ensure ransomware payment is legal
If you are forced to pay the ransom to recover critical files, how do you ensure that you will not incur any legal consequences or hefty fines for making an illegal ransom payment?
Ransomware payments are becoming increasingly regulated to ensure ransom payments are not made to any nefarious or sanctioned entities that pose a risk to national security.
Working with a ransomware recovery service that follows an up to date sanctions compliance program can give you the peace of mind that you need to ensure your ransom payment is made within the confines of the law.
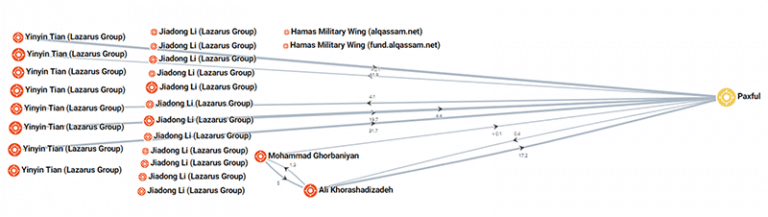
Sanction compliance programs can use a screening process that screens the following:
- Ransomware variant name – to ensure no current sanctioned entities are associated with the variant
- IP address of the attacker – to ensure the attacker is not from a sanctioned country
- Bitcoin wallet of the attacker – to utilize tracing software and ensure the bitcoin wallet isn’t linked to any of the bitcoin wallets on the Specially Designated Nationals and Blocked Persons (SDN) list
- IP address of email headers – to ensure the attacker is not from a sanctioned country
5. Expedited acquisition of cryptocurrency to facilitate a ransom payment
When your business critical data is encrypted and you are forced to pay the ransom, you need to quickly complete the transaction to avoid the ransom amount potentially increasing or the threat actor changing their mind.
Some ransomware variants such as Sodinokibi ransomware will automatically double the demanded ransom amount if the ransom is not paid within a set amount of time.
The typical length of time it takes to verify your identity, purchase, and process bitcoin from a cryptocurrency exchange can take an extended period of time depending on which exchange you utilize.
A ransomware recovery service should have established relationships with cryptocurrency exchanges to ensure funds are readily available to pay your ransom the moment your business needs it most.
Additionally, acquiring bitcoin on your own can pose security risks unless you purchase bitcoin through a well-vetted entity that will not scam you. Sending digital currency, the right amount, and to the right wallet, can also pose a risk for you if you haven’t done anything like that previously.
If you require urgency and experience then using a ransomware recovery service is paramount to get the job done quickly and efficiently.
6. Experience with troubleshooting decryption tools
Some variants require multi-stage decryption processes which are more complicated than others.
For instance, when a Dharma ransom demand is paid, the hacker will provide an initial ransomware decrypter scanning tool that scans all your files for a public key.
Upon receiving the scanning tool, you must scan all your encrypted ransomware files and send the public key back to the hacker who will produce a unique private decryption key to unlock your files.
Unfortunately, this intermediary step requiring a scan for a public key complicates the ransomware recovery process, especially for ransomware attacks that have infected numerous devices on your network.
What the attacker doesn’t tell you is that if you don’t have all your encrypted files attached to the same device during the first scan, they will ask for an additional ransom payment for another scan.
A ransomware recovery service has experience working with various decryption utilities to help prevent unexpected costs in the process.
Some companies may even extract the decryption key from the hacker tool and use it in their own custom tool that has better functionality. In turn, you will be able to restore your data faster with a better recovery rate.
7. Learn about the scope of the ransomware attack with a remote evaluation
If you are concerned whether working with a ransomware recovery service is worth the cost, most recovery companies will provide you with a evaluation before making any commitments.
A ransomware evaluation will provide you with details about your specific ransomware incident and available recovery options without costing a cent.
A ransomware evaluation will:
- Identify the ransomware variant or variants
- Identify whether there are multiple layers of encryption
- Attempt to discover the attack vector used to deploy the ransomware
- Determine if the malware encryption is breakable
- Identify whether the threat actor group is known to remove data while on your network
- Determine if encrypted files are partially encrypted and can be repaired
- Outline your options for data recovery and the associated costs
The initial ransomware evaluation can be used as the building blocks of a ransomware forensics investigation if you need an in depth report of how your network was breached and whether any data was accessed or removed from the network.
8. Security recommendations to prevent repeat attacks
A ransomware recovery service will typically have experience responding to many different kinds of ransomware and can therefore provide recommendations to prevent future cyber attacks.
This is especially true if the ransomware recovery company has performed digital forensics in response to ransomware attacks. When you are able to discover how the attacker gained access to your network, you then know what you have to do to better protect yourself.
In addition, you will be provided with educational resources that can be shared with your staff to avoid future ransomware occurrences. Educating your workforce about ransomware is an important aspect to prevent future ransomware attacks.
Remember, your security is only as strong as your weakest link.
How do I know if I should use a ransomware recovery service?
You’ve read about the biggest benefits of a ransomware recovery service, so now you need to decide if you want to start working with a company.
Still not sure if using a ransomware recovery service is right for you?
Ransomware recovery services are a great fit for someone who:
- Needs to recover from a ransomware attack quickly
- Wants to be able to make informed decisions based on data gathered from previous similar ransomware incidents
- Wants to know if their files can be repaired or decrypted without paying the ransom
- Does not have prior experience negotiating ransom demands or acquiring cryptocurrency for ransom payments
- Isn’t up to date on all active ransomware variants
- Does not know which ransomware attackers are sanctioned and subsequent ransom payment is illegal
- Needs to know how to remove the virus and prevent future attacks
Ransomware recovery services may not be a good fit if:
- You are aware of all the recovery options available
- Have reliable data on ransomware actors you can use to make informed decisions
- You have experience with negotiating ransom amounts and acquiring cryptocurrency
- You have a complete understanding of evolving sanction compliance
- Have a game plan for removing the ransomware and making the necessary patches
- You want to restore from a backup or recreate your data and remediate the environment on your own
At Proven Data, we have helped thousands of clients recover their files after a ransomware attack.
Our full range of ransomware recovery services have you covered from start to finish; we can help with ransomware incident response, data recovery, ransomware forensics, and cyber security to prevent future attacks.
Our ransomware recovery experts have the experience you need to get your business back up and running in the shortest time possible and keep your business protected moving forward.
Need ransomware help now or want to learn more?
Reach out to one of our ransomware recovery specialists today!
Request a Ransomware Recovery Evaluation







