You’ve arrived at this page because of your curiosity in cyber security and data protection. You understand how critical it is to keep your data safe from threats such as malware and ransomware, and want to take action to protect your business assets.
Proactive planning is one of the first steps you can take to improve your organization’s cyber security. Optimizing your endpoint detection and response (EDR) security protection is a fundamental step to begin securing your organization from cyber attacks. But what is endpoint security protection, and how does it work?
As a cyber security service provider, our goal at Proven Data is to find the cyber security solution that is right for your business. With over 20 years of cyber security experience, our team of experts has helped clients from a wide range of cyber-related issues find the right cyber attack prevention solutions to fit their organizational needs.
By the end of this article, you will better understand what endpoint security is, how it works, and if it’s right for your business. Not every organization will need the full-scale of endpoint security, and we are here to outline the features and benefits of Endpoint Detection and Response (EDR) software if you choose that method to protect your data.
What is endpoint security?
To understand if EDR is right for your organization, you must comprehend how it’s related to the concept of endpoint security.
Endpoint security is the discipline of protecting connected devices on an organization’s network. The application of endpoint security can help businesses secure multiple devices and offer advanced visibility into network events.
This cyber security approach has grown exponentially over the past few years.

What is an endpoint?
Endpoints are the connected devices and individual computers in which your employees use to get their work done.
Endpoints continue to grow in numbers for companies as more businesses use connected devices and computers to carry out their product or service lines for their clients.
Common endpoint devices include:
- Desktop computers
- Laptops
- Mobile phones
- Connected smart devices
- Servers

Think about your company and how many endpoints you have and who is accessing data at your organization.
What is EDR?
Endpoint Detection and Response (EDR) is a modern security solution that focuses on securing a network and enhancing connected endpoints’ visibility. The use of a centralized management system helps organizations respond to cyber threats more efficiently.
With this increased visibility, EDR helps businesses prevent malware, ransomware, and malicious activity on their network.
The term EDR can be traced to security researcher Anton Chuvakin for Gartner in 2013 to describe the tools primarily focused on detecting and investigating suspicious activities (and traces of such) other problems on hosts/endpoints.
Endpoint Detection and Response is also sometimes referred to as:
- EDTR (Endpoint Detection and Threat Response)
- ATP (Advanced Threat Protection)
Although the security solution features may vary from each developer, these terms generally characterize the goal of the product. Endpoint Detection and Response tools operate by auditing events on a network and registering them with a centralized database.
This database keeps a watchful eye on possible threats by comparing them to previous known attacks.
4 fundamental basics of how endpoint detection and response (EDR) works
Although the features and interface of various EDR solutions may vary, they all adhere to a comprehensive approach for managing cyber threats. Endpoint Detection and Response security platforms use a process that works to detect, contain, investigate, and eliminate malicious cyber threats like ransomware and malware. EDR solutions provide a centralized method in which an organization can monitor endpoints and respond accordingly to keep them secure.
#1. Detection
The most critical step of any EDR solution is its ability to identify and recognize when there is an incoming threat to the network and your connected endpoints. These early warning signs trigger an alarm and block the malware from entering before it causes more damage.
But how does the EDR solution know there is malware incoming to the network?
Endpoint Detection and Response platforms leverage threat intelligence that helps the software learn & respond to the most advanced and modern malware threats.
Think about a security checkpoint at the airport and how they use data, facts, and evidence from previous incidents to make their processes better and more secure for other passengers.
This data feed helps harden the system and make improvements. By understanding precisely the types of threats and how they affect your endpoints, the software can help block similar danger when it sees it.
Your EDR solution relies on the strength of good threat intelligence and security professionals who design the system.
#2. Containment
Malware authors are becoming more sophisticated and better at what they do. The malicious software they design can sometimes sneak by the detection phase and begin to target the endpoints with ransomware, where files can be encrypted.
The containment phase of EDR reduces as much damage as possible if the malware does affect your network. By containing the threat to fewer endpoints, the malware has less chance of causing widespread destruction of the company’s data.
EDR solutions control the spread of ransomware and cyber threats. Because the endpoints are communicating in tandem, they effectively contain and prevent malware spread to other parts of the network.
Organizations can further reduce their risk by ensuring their network is segmented and proper access controls are in place.
#3. Investigation
EDR solutions use a security technique called sandboxing that allows the software to test a copy of a suspicious file outside the network for authenticity. If determined to be safe, the file is released back on the network.
#4. Elimination
Endpoint protection has your back where it matters the most… removing the cyber threat efficiently and effectively. Once the EDR software concludes the malicious files are a hazard to your endpoints’ cyber security, it eliminates the malware.
The EDR makes executions such as:
- Removing replicated or hidden malicious files
- Scanning network for similar malicious files
Think of an endpoint security platform working as a 24/7 security guard that helps you catch, expose, and eliminate the thieves trying to get into your storefront.
Why is endpoint protection important?
Cyber security threats are beginning to evolve in significant ways, as cyber adversaries continue to improve their malware and increase its effectiveness. Hackers find more creative and unique ways to enter a network, and the endpoints are their ultimate target.
These advanced threats require a modern, substantial security solution, and endpoint security fills that vulnerability gap.
Endpoint detection and response helps keep your business safe by:
Actively tracking incoming threats
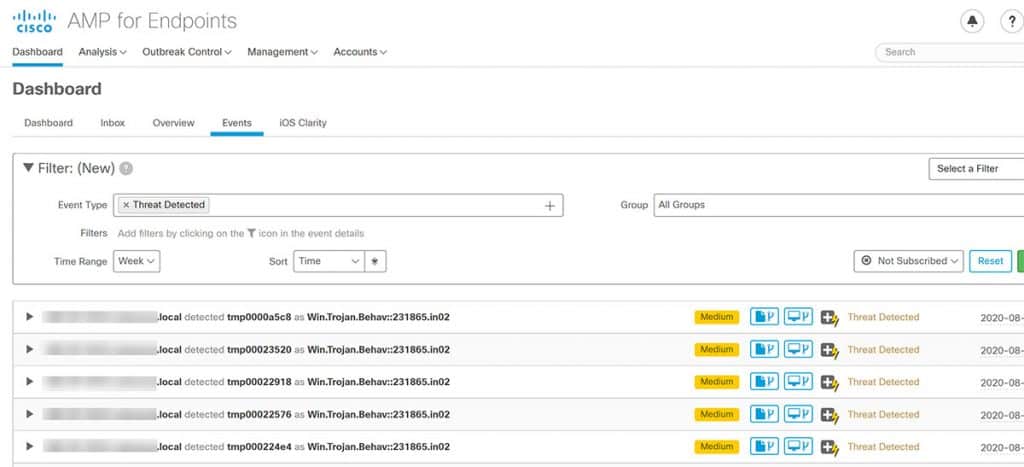
One of the main features of an endpoint security solution is that it alerts system administrators of incoming threats in real-time. Time is not on your side when responding to a cyber attack, and every second counts when there’s possible malware at the front door.
Dashboards and oversight tools allow you to see in detail the security alerts that can affect your business.
Protecting from multiple cyber attacks at once
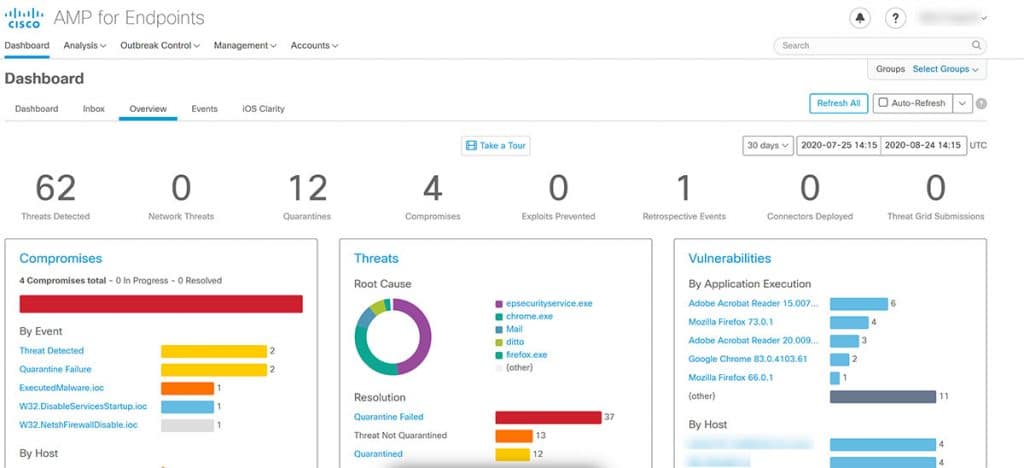
Cyber attacks such as ransomware are becoming increasingly stealthy and difficult to track from one endpoint. EDR does an excellent job of examining security incidents related to all connected endpoints, and identifying to eliminate these threats.
If your business is under cyber siege from many angles, the increased visibility of endpoint security can help defend against and control the virus(es).
Common features in endpoint security
Although endpoint protection is a relatively new security concept of the last decade, it is exploding in market share with many different vendors and products available for purchase. Each of these implementations of endpoint security is built on the threat intelligence that their developers gather.
Although the look and feel of EDR solutions may vary, you must decide what best works for your organization. If you are a regulated industry, certain features like endpoint encryption may be desirable. Common EDR features include:
- Network access management & controls: Dashboard where system administrators can easily add and remove new endpoints to the platform.
- Application whitelisting: Set which applications are safe for users to launch and block applications that may pose a threat.
- Endpoint encryption: Keep the files on an endpoint secure by encrypting the machine which adds another layer of protection in case the data does become compromised.
What are the differences between EDR and antivirus?
There is a lot of confusion about the main differences between EDR and traditional antivirus solutions. Although both keep you and your network secure from malware and outside threats, some key differences might determine which is better for your needs.
Here are 3 key differences between EDR and antivirus:
Level of Protection
The first and foremost largest difference between the two cyber solutions is that EDR examines security threats of a network, while antivirus is only reliable for one endpoint. Traditional antivirus software relies on signature-based matching, while EDR uses analysis and data to predict advanced threats.
EDR is much more scalable than antivirus, in which new endpoints and networks are added over time as the company grows. Antivirus offers protection for businesses on a small scale with much less control.
Learning Curve
Traditional antivirus software is classic “set it and forget it” that will require you to install and update the software when it is needed. There is no additional security monitoring that needs to be done by the user.
Endpoint Detection and Response solutions require a much more involved approach to protect your business.
To maximize the benefits of EDR, you should be monitoring regularly for detections. Early detection helps you to respond quickly before damage is inflicted. You can either have a cyber security company install and monitor your network, or monitor on your own (which will affect costs below).
Cost
Comparatively, EDR is more expensive than traditional antivirus business solutions. For traditional antivirus, it’s usually as simple as pay, download, and install the software. If you know how to install the software yourself, this can save you from paying an outside provider.
Endpoint Detection and Response software costs more than traditional antivirus because of the centralized management features and advanced capabilities.
If you aren’t able to install and configure the software yourself, you may pay a fee to an outside resource. Configurations for EDR tend to be more complicated than traditional antivirus.
Costs also vary depending on whether an independent security company contracted to monitor the EDR for you.
Is endpoint detection and response a good fit for my business?
To a person just finding out about Endpoint Detection and Response, this may all sound foreign and may not know if this is the right fit for your company. How can an all-in-one solution add so much protection against ransomware and malware on my network?
There is no silver bullet when it comes to cyber security and protecting your business from malware and ransomware. We don’t want to give you the false hope that applying Endpoint Detection and Response will eliminate all your cyber security risks. However, it’s a step in the right direction.
The best cyber security programs require a layered approach that fits the needs of the organizations seeking protection. At Proven Data, our cyber security experts are passionate about finding solutions that close that fit the needs of your organization that ultimately keep your business secured.
Our proprietary threat intelligence enables IT Leaders to make informed decisions utilizing data from the front lines. Additionally, our experience in ransomware recovery and digital forensics helps you understand where your company may be most vulnerable and how you can close those vulnerabilities and prevent a cyber attack.
Interested in what it will cost to use endpoint detection and response at your business? Our cyber security cost guide outlines what to expect for EDR expenses and fees.
Maybe you would like to know more about EDR and if it’s right for your organization? We’re here to help you make an informed decision. Open a case or call Proven Data to get started.
Need network security solutions now?
Take action to protect your network and data from malware threats!
Request a cyber security consultation







