The Daixin Team is a formidable ransomware and data extortion group that has emerged as a significant cyber threat. It particularly targets the Healthcare and Public Health (HPH) sector since at least June 2022.
Its systematic approach to targeting healthcare organizations, encrypting critical servers, and exfiltrating sensitive data, creates a dual-layered impact that amplifies the severity of its attacks.
Daixin extortion group overview
The Daixin team’s strategic compromise of privileged accounts allows them to breach VMware vCenter Servers, reset passwords for ESXi servers, and subsequently deploy ransomware.
According to CISA, the group’s focus on healthcare organizations is driven by the lucrative nature of healthcare data on the dark web.
Its historical attacks have positioned Daixin as a significant concern in the ongoing battle against ransomware. It illustrates the need for robust cybersecurity measures and heightened vigilance within targeted sectors.
How to identify Daixin ransomware
Indicators of compromise (IOCs) are pieces of forensic data that can help identify malicious activity or malware associated with a cyber attack. It includes the encryption extension, file hashes, and IP addresses, among other details cyber criminals leave as they infect a machine or system.
But, if you can’t identify the ransomware strain through its IOCs, you can use Proven Data’s free ransomware ID tool to check if the Daixin ransomware is the malware that encrypts your files.
Important: Some of these indicators require technical knowledge of the infected system, so you may need to contact your IT team or a digital forensics service provider.
Daixin team IOCs include:
You can identify a Daixin attack in its early stages by its SHA-256 hash files.
SHA-256, Secure Hash Algorithm 256-bit, is a cryptographic hash function that belongs to the SHA-2 family of hash functions. It’s designed to take an input message and produce a fixed-size output hash value of 256 bits (or 64 hexadecimal characters).
A hash is a function that takes an input (or ‘message’) and produces a fixed-size string of characters. The output, known as the hash value or hash code, is unique to the input data.
SHA-256 is used in various security applications and protocols, including digital signatures, certificate generation, and integrity verification.
The SHA256 hashes associated with Daixin Team:
- 9E42E07073E03BDEA4CD978D9E7B44A9574972818593306BE1F3DCFDEE722238
- 19ED36F063221E161D740651E6578D50E0D3CACEE89D27A6EBED4AB4272585BD
- 54E3B5A2521A84741DC15810E6FED9D739EB8083CB1FE097CB98B345AF24E939
- EC16E2DE3A55772F5DFAC8BF8F5A365600FAD40A244A574CBAB987515AA40CBF
- 475D6E80CF4EF70926A65DF5551F59E35B71A0E92F0FE4DD28559A9DEBA60C28
How Daixin ransomware works
The Daixin Team ransomware operates through a multi-step process that involves gaining unauthorized access to systems, deploying encryption on critical servers, exfiltrating sensitive data, and then demanding a ransom for the restoration of services and prevention of data exposure.
Here is an overview of how the Daixin ransomware works:
1. Initial Access
gains initial access through virtual private network (VPN) servers, employing techniques such as exploiting vulnerabilities in VPN servers, phishing emails, and exploiting the absence of Multi-Factor Authentication (MFA).
2. Lateral Movement
Once inside the target’s network, Daixin actors move laterally using Secure Shell (SSH) and Remote Desktop Protocol (RDP).
They leverage privileged accounts acquired through credential dumping and pass-the-hash techniques to gain access to VMware vCenter Servers.
3. Ransomware Deployment
The ransomware, based on leaked Babuk Locker source code, specifically targets ESXi servers and encrypts files with extensions like .vmdk, .vmem, .vswp, .vmsd, .vmx, and .vmsn.
4. Data Exfiltration
Before encrypting systems, Daixin actors exfiltrate personal identifiable information (PII) and patient health information (PHI) from victim systems.
Exfiltration methods include using tools like the Rclone, an open-source file management program, and Ngrok, a reverse proxy tool.
5. Drop off the Ransom Note and Extortion
The Daixin Team ransom note includes a threat to publicly the exfiltrated data within a 5-day timeframe unless the stipulated ransom is paid. Additionally, the victims are provided with a unique personal PIN, intended for communication with the threat actors.
Important: Do not pay the ransom. Paying the ransom does not guarantee that you will get your data back, and it may encourage the attackers to continue their criminal activities. Check our in-depth article on what happens if you pay the ransom.
How to handle a Daixin ransomware attack
It is important to note that handling a ransomware attack can be complex and requires expertise. Therefore, it is recommended to seek professional help from a reputable data recovery service, such as Proven Data to help you recover your data and remove the ransomware from your system.
You can also report the attack to law enforcement agencies, such as the FBI, and cybersecurity organizations to help prevent future attacks and catch the perpetrators.
We strongly recommend contacting cybersecurity services to handle ransomware attacks. Proven Data technicians not only retrieve ransomware-encrypted data but also create forensic reports and streamline incident response, minimizing your business downtime and financial loss.
Notable attacks by Daixin ransomware
The impact of the Daixin attacks extends beyond financial losses, affecting patient care, operational efficiency, and data security.
The three attacks described here underscore the Daixin Team’s focus on targeting healthcare institutions and other sectors, leading to data breaches, ransom demands, and disruptions to critical services.
Ontario Hospitals
The Daixin Team claimed responsibility for a ransomware attack that targeted five hospitals in Ontario, Canada, on October 23, 2023.
The affected hospitals include Bluewater Health, Chatham-Kent Health Alliance, Erie Shores HealthCare, Hôtel-Dieu Grace Healthcare, and Windsor Regional Hospital.
The attack led to the disruption of hospital activities, rescheduling of appointments, and data exposure impacting approximately 5.6 million patient visits.
AirAsia
Daixin was reportedly behind a major ransomware attack on AirAsia in November 2022. The details of the attack and its impact on the airline’s operations are not provided in the gathered information.
OakBend Medical Center
Daixin targeted OakBend Medical Center in September 2022. The cyberattack resulted in weeks of network downtime and the alleged theft of patient health information from the hospital’s internal servers.
Data proofs of the stolen data were leaked on the Daixin dark website.
How to prevent ransomware attacks
Preventing Daixin ransomware attacks is always the best cybersecurity tactic. If you are a recent victim, you must follow these tips to avoid a new ransomware attack:
Keep your software up to date
Regularly update your operating system and programs to uphold security standards. Reputable OS providers will consistently check their software for vulnerabilities and patch their security standards to protect against newly detected threats.
Use reputable antivirus software
Employ reputable antivirus software to bolster protection against malware significantly, and regularly check that it is updated. You can also check your network for vulnerabilities and learn where you need to improve your security system.
Be cautious of suspicious emails
Even though there are no known cases of Daixin using phishing as an attack method, it’s important to exercise caution when dealing with emails from unfamiliar or dubious origins. Refrain from opening files or clicking on links within emails that you are not expecting or seem suspicious.
Do not download cracked software
Cracked software is the term used to describe illicitly modified or pirated versions of commercial software, typically distributed without proper authorization or licensing. Cybercriminals frequently conceal their ransomware executables within cracked software distribution websites, leading users to download and execute the malware unwittingly.
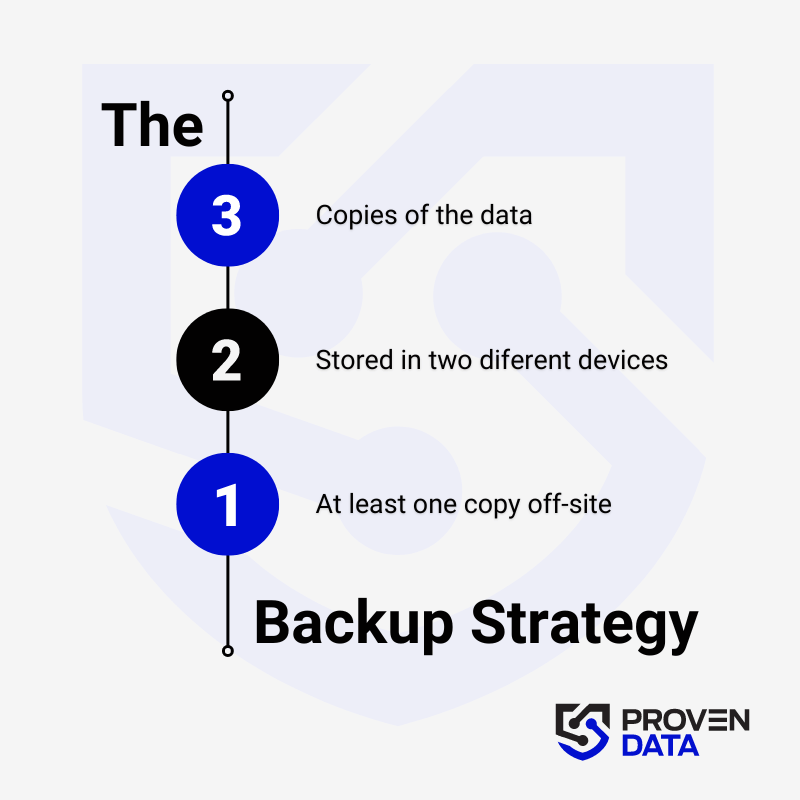
Backup your data
Regularly back up your data to an external hard drive or cloud storage service to prevent complete data loss in case of a ransomware attack. A highly recommended strategy for data loss prevention is the 3-2-1 backup strategy.
The 3-2-1 backup strategy involves creating three total copies of your data: two on different media and one offsite, ensuring redundancy and protection against data loss. And at least one copy offsite to prevent loss due to natural disasters or other local incidents.
Educate yourself and your teams
Educate yourself and your employees about the risks of ransomware and how to avoid it, such as avoiding suspicious emails or downloads.
Consult cybersecurity professionals
Proven Data offers cyber security services to help you keep your data protected against threat actors. From vulnerability assessment to ensure your systems and servers do not have open doors for cyber attacks, to Incident Response (IR) services for immediate response in case of a successful attack.
We also have the option of managed detection and response (MDR) services that help organizations improve their security posture, minimize risk, and protect sensitive data and assets.







