
What is Outsourced Cyber Security? Pros and Cons
What are the pros and cons of outsourced cyber security services? Learn about why you need to invest in cyber security and find out if outsourcing is the right choice for your security needs

What are the pros and cons of outsourced cyber security services? Learn about why you need to invest in cyber security and find out if outsourcing is the right choice for your security needs

What are the benefits of endpoint detection and response and why is it important? Discover how this powerful cyber security product works and the various ways it helps protect your business from ransomware and malware.

How do you secure your network in the data following a ransomware attack? Discover the best practices for securing your network after a cyber attack and the costs associated with strengthening your cyber security.
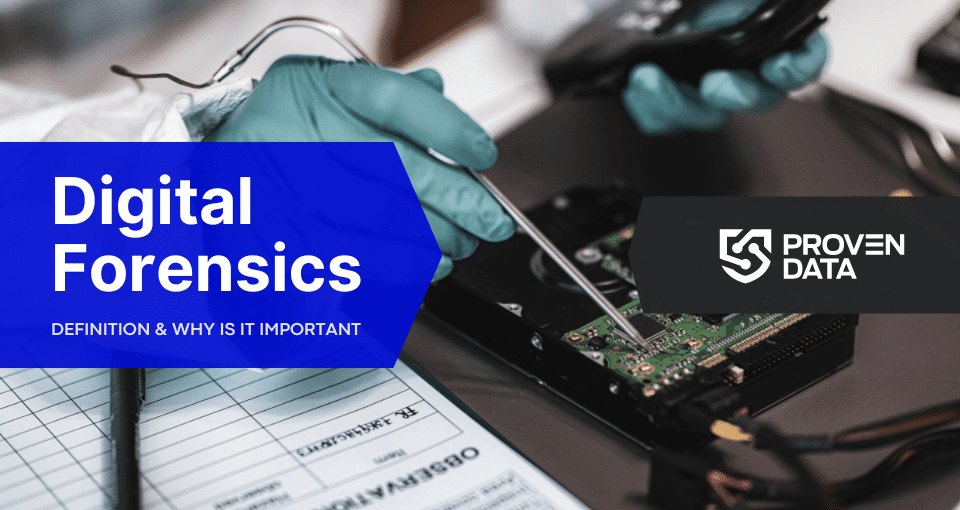
Understand how a digital forensic investigation can help you learn what happened after a cyber attack. Discover how digital forensics is used to follow the tracks of a ransomware attack or cyber threat on your network. Protect your data in the future by learning what happened during a cyber attack.

How do you choose the right cyber security company? Here are the top 5 traits to assess the best cyber security solution for you. Learn what to look for in a cyber security company that will meet your needs.

How does a ransomware attack happen? Here are 3 common ways your files are encrypted or locked in a ransomware attack. Find out how the ransomware encrypts your files by remote desktop protocol, phishing attacks, and exploit kits. Learn where ransomware comes from and how to prevent ransomware.

How much does cyber security cost? Explore the costs and rates for cyber security products and services, and keep your business protected against cyber threats like ransomware.

Find out how your files were encrypted with ransomware. Learn about the methods for ransomware recovery and restoring business operations. See if how you can unlock your files from ransomware and methods to ransomware recovery.

How is Proven Data helping to provide COVID-19 relief as a result of the pandemic? Learn how we strive to help participate in combating global cyber threats.

What cyber threats are happening as a result of the coronavirus? Learn about how you can keep safe from cyber attacks during COVID-19.
If you suspect data loss or network breach, or are looking for ways to compile digital evidence through forensics and eDiscovery services – our team can help.
Our expert advisor will contact you to schedule your free consultation.
You’ll receive a customized proposal or quote for approval.
Our specialized team immediately jumps into action, as time is critical.