The U.S. Cybersecurity and Infrastructure Security Agency (CISA) released an alert announcing a massive hack including “compromises of U.S. government agencies, critical infrastructure entities, and private sector organizations by an advanced persistent threat (APT) actor beginning in at least March 2020”.
The joint statement released by CISA, the Federal Bureau of Investigation (FBI) and the Office of the Director of National Intelligence (ODNI) follows a SolarWinds notification on Dec. 12 to its 33,000 customers that an “outside nation-state” had found a back door into updated versions of the Orion software.
How did the massive hack occur?
The compromises were initially reported as exploiting the SolarWinds Orion Platform software versions 2019.4 HF 5 through 2020.2.1 HF 1, released between March 2020 and June 2020.
CISA’s Dec. 13 emergency directive instructs all federal agencies to disconnect the affected Orion products from their networks immediately. CISA has signified that the threat presents a grave risk to the federal government.
The directive states that the vendor is working to provide updated software patches, but CISA is instructing SolarWinds users to wait to reinstall SolarWinds Orion software until further guidance is provided regarding the patches.
SolarWinds supports a massive, high profile client list including:
- Over 425 of the U.S. Fortune 500 companies
- All ten of the top ten US telecommunications companies
- All U.S. military branches
- All five of the top-five U.S. accounting firms
- The Pentagon
- The State Department
- The National Security Agency
- The Department of Justice
- The White House
Additionally, CISA has indicated evidence of access vectors other than the SolarWinds Orion platform, including a flaw in software virtualization platform VMware, according to Krebs On Security.
The U.S. National Security Agency (NSA) warned on Dec. 7 that Russian hackers were using the VMware platform to impersonate authorized users on victim networks.
Furthermore, the massive hack is suspected to be linked to a breach at FireEye, a U.S. cyber security company that said the hack it experienced was identified as a part of a global campaign targeting governments and businesses by infecting SolarWinds updates with malware starting in the spring of 2019.
Who is responsible for this massive hack?
Reuters reported that the hackers responsible for the attack are suspected to be working for Russia. The hackers’ actions initially went undetected as they reportedly tampered with SolarWinds Orion updates.
Additionally, Reuters reports the hackers are connected to monitoring U.S. Treasury and Commerce departments’ internal emails. The attackers also targeted key personnel, incident response staff, and IT email accounts, according to CISA.

Why is this hack important to me?
This incident points to the need for proactive cyber security measures by all organizations. If top security companies and government entities can be breached and derailed by an attack such as this, a smaller organization truly cannot sustain experiencing an incident of similar magnitude.
While government entities and Fortune 500 companies might seem like hot targets, unfortunately, small businesses are similarly at risk of being cyber crime targets.
Small business are perfect targets for attackers for reasons including:
- Smaller cyber security budget
- Less sophisticated security protections
- Lack of dedicated security departments and personnel
- Connections to larger organizations which may be the end goal of the hack
Cyber security does not have to be complicated, but it must be continuously improved and updated as the threat landscape evolves.
What can I do to protect myself from a similar hack?
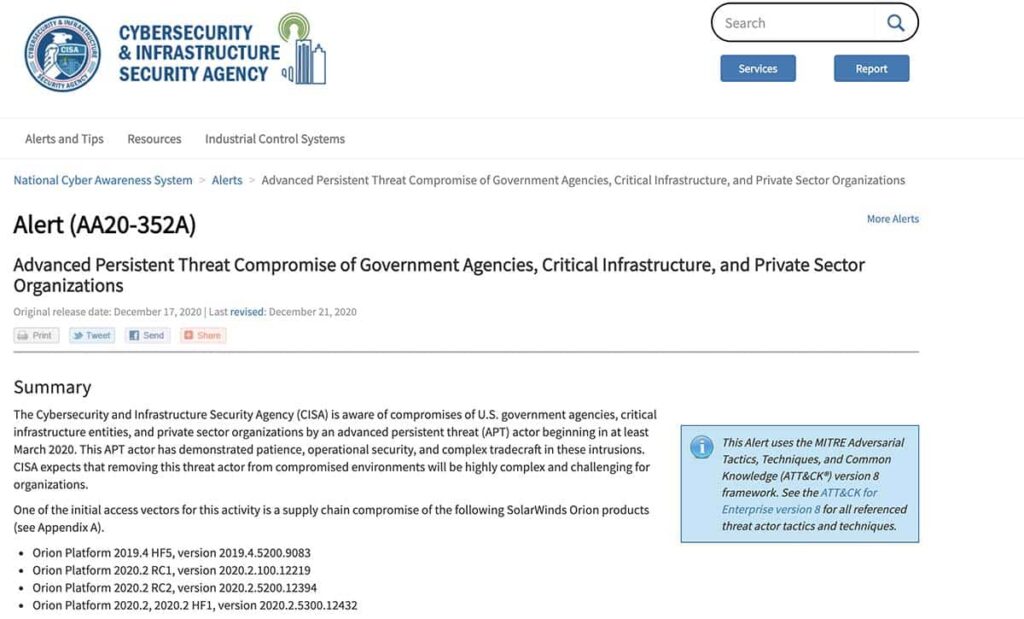
CISA’s alert detailed operational security measures that should be taken to mitigate risk, including:
Operational security plans should include:
- Creating out-of-band communications guidance for staff and leadership
- Outlining what “normal business” is acceptable to be conducted on the suspect network
- Maintaining a call tree for critical contacts and decision making
At Proven Data, our team of cyber security experts are on call 24/7 to assist you in attack mitigation and remediation.
Need cyber security assistance?
Speak to one of our experts today.
Request a cyber security consultation







