Trigona ransomware emerged in late 2022 and represents a sophisticated and evolving threat in the realm of cybersecurity. Its modus operandi is to encrypt the data of its victims, rendering it completely inaccessible without the decryption key.
Once the files are encrypted, Trigona demands a ransom payment from the victims for the decryption key. This form of extortion targets individuals, businesses, and organizations alike, causing significant disruption and data and financial losses.
This in-depth guide explores the Trigona ransomware offering a comprehensive explanation of its characteristics and associated indicators of compromise (IOC). Understanding the industries Trigona targets and gaining insight into its operational tactics are crucial in enhancing cybersecurity and fortifying defenses against ransomware attacks.
Trigona ransomware overview
Trigona employs advanced encryption techniques, primarily relying on AES encryption. Moreover, it may include functionality to wipe data and steal credentials, utilizing tools such as Mimikatz.
Notably, Trigona is notorious for its double extortion tactics, where it exfiltrates sensitive data before encrypting it, amplifying the impact of its attack. The attackers will then threaten to expose the stolen data in their TOR website unless victims comply with their demands.
Written in the Delphi programming language, Trigona exhibits a level of sophistication that underscores the evolving landscape of cyber threats.
How to identify Trigona ransomware: main IOCs
Indicators of compromise (IOCs) are forensic clues crucial for identifying malicious activity or malware linked to a cyber attack.
These include encryption extensions, file hashes, and IP addresses, among other details left behind by cybercriminals during a system or machine infection.
It’s important to note that some of these indicators may necessitate technical expertise about the infected system, prompting you to seek assistance from your IT team or a digital forensics service provider.
Pro tip: If you struggle to identify the ransomware strain using IOCs, Proven Data offers a free ransomware ID tool.
Trigona ransomware-specific IOCs include:
These IOCs can be used to identify and potentially mitigate Trigona ransomware attacks.
- File Hashes (SHA256)
File hashes are unique digital fingerprints created for each file. When ransomware encrypts a file, the hash completely changes. By comparing the hash of an encrypted file to a database of known ransomware variants, you can identify the specific strain responsible for the attack.
- 8cbe32f31befe7c4169f25614afd1778006e4bda6c6091531bc7b4ff4bf62376
- efb688214c3fe5d9273ec03641cf17af5f546b11c97a965a49f8e617278ac700
- f64211b0a49589bb53523dfb88eb9937ab88c8fcea98e2aabcbee90f1828e94e
- 11b0e9673bbeb978aa9b95bcad43eb21bbe0bbaaf7e5a0e20d48b93d60204406
- eda603f4d469d017917f5d6affeb992fdf3b7971e49868ece8c38fb8e6f8b444
- c4529a061f205aaee46c219123d15059d2161df2bd7c7b738dd2a2c1ffd8d3ee
- 170fa5d29cdb562d41a054abf2a57ca29fc233805b59692a1a57ebf25449be7c
- f29b948905449f330d2e5070d767d0dac4837d0b566eee28282dc78749083684
- 197f4933680a611ad2234a22769bd079885f81956221ec0de172d5a19eab648e
- 1017fcf607a329bb6ad046181c3656b686906a0767fff2a4a3c6c569c2a70a85
- 761b78ddab55b4e561607ce5ce9d424a7aec4f1994aad988f0612b096cdd1d6d
- 097d8edb1762d7d3ded4360a9f5b4673a898937421f36853d2f5cde77e1bac93
- 4a06231957c53dee1a11ff3eb84caad082f18761aee49e72d79c7f1d32884e34
- File Extensions: .\_locked.
- Command-Line Parameters:
- – /full
- – /!autorun
- – /test_cid “test”
- – /test_vid “test”
- – /p, /path “path”
- – /!local
- – /!lan
- – /autorun_only “path”
How Trigona ransomware works
Trigona ransomware operates through a series of steps designed to encrypt files on Windows systems, extract sensitive information, and extort victims for ransom.
Overall, Trigona ransomware presents a sophisticated and evolving threat to Windows systems, combining advanced encryption techniques, credential theft, and extortion tactics to target organizations across various industries.
1. Initial Access
Trigona ransomware gains initial access to a victim’s environment through various means, including exploiting vulnerabilities, conducting active reconnaissance, and transferring malware via remote monitoring and management (RMM) tools.
2. Credential Theft
Trigona employs the Mimikatz exploitation tool to perform credential loading, dumping, manipulation, and injection. Mimikatz retrieves credentials from Windows memory, the Local Security Authority Subsystem Service (LSASS) process, and the Windows registry.
3. File Encryption
Trigona utilizes a combination of RSA and AES encryption techniques to encrypt files on both local and network drives. The ransomware encrypts files with a 4,112-bit RSA public key and a 256-bit AES symmetric key in Output Feedback (OFB) mode. Encrypted files are appended with the extension .\_locked.
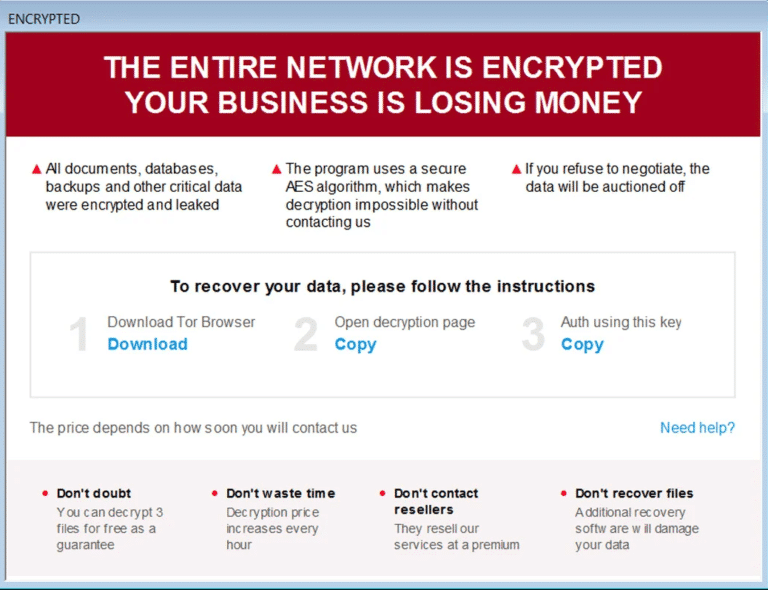
4. Ransom Note Delivery
Unlike traditional ransomware notes, Trigona delivers its ransom note in the form of an HTML application with embedded JavaScript.
The ransom note contains Computer IDs (CIDs), Victim IDs (VIDs), email addresses for communication with the attackers, and TOR URLs for negotiation.
Important: Paying the ransom does not guarantee that you will get your data back, and it may encourage the attackers to continue their criminal activities. Check our in-depth article on what happens if you pay the ransom.
How to handle a Trigona ransomware attack
Dealing with a ransomware attack requires specialized expertise. Thus, it’s advisable to enlist the assistance of a trusted data recovery service like Proven Data to aid in data recovery and ransomware removal.
Another important step is reporting the attack to law enforcement bodies such as the FBI and cybersecurity organizations to thwart future attacks and apprehend those responsible.
Proven Data technicians excel not only in recovering ransomware-encrypted data but also in producing forensic reports and optimizing incident response, thereby reducing business downtime and financial impact.
Who does the Trigona ransomware target
Trigona ransomware victims represent a diverse range of industries, including manufacturing, finance, construction, marketing, and high technology. These sectors encompass a wide array of organizations, from small businesses to large corporations.
Manufacturing: Companies involved in manufacturing processes, such as automotive, aerospace, electronics, and consumer goods production, are potential targets. Trigona may aim to disrupt production lines, steal proprietary designs or sensitive information, and extort ransom payments.
Finance: Financial institutions, including banks, investment firms, insurance companies, and accounting firms, are attractive targets due to the sensitive financial data they possess. Trigona may seek to encrypt customer records, financial transactions, and other critical data to disrupt operations and extort money.
High Technology: Technology companies, including software developers, IT services providers, and telecommunications firms, are lucrative targets for ransomware attacks. Trigona may aim to encrypt proprietary software code, customer databases, network infrastructure information, and research and development data to extract ransom payments.
How to prevent Trigona ransomware attacks
Preventing Trigona ransomware attacks is always the best cybersecurity tactic. By implementing these preventive measures and fostering a culture of cybersecurity awareness, organizations can significantly reduce their risk of falling victim to Trigona ransomware attacks and other similar threats.
Important: To be effective, you must ensure that human errors are minimal, as users may unintentionally let malware infect the system.
Consult cybersecurity professionals
Proven Data offers cyber security services to help you keep your data protected against threat actors. From vulnerability assessment to ensure your systems and servers do not have open doors for cyber attacks, to Incident Response (IR) services for immediate response in case of a successful attack.
We also have the option of managed detection and response (MDR) services that help organizations improve their security posture, minimize risk, and protect sensitive data and assets.
Software updated
Regularly update operating systems, software applications, and firmware to patch known vulnerabilities. Vulnerabilities in outdated software can be exploited by ransomware like Trigona to gain unauthorized access to systems.
Implement strong access controls
Enforce the principle of least privilege by providing users with only the permissions and access levels necessary to perform their job functions. Restrict administrative privileges to prevent unauthorized software installations and modifications.
You can also segment your network into separate zones with firewalls and access controls to contain the spread of ransomware infections.
Backup regularly and securely
Maintain regular backups of critical data and ensure that backups are stored securely offline or in a separate, isolated network environment. Backup solutions should be automated, encrypted, and tested regularly to ensure data integrity and availability in the event of a ransomware attack.
Educate employees
Provide cybersecurity awareness training to employees to help them recognize phishing attempts, suspicious websites, and social engineering tactics used by ransomware operators. Encourage employees to report any unusual activity or potential security threats promptly.
Develop an Incident Response Plan
Establish an incident response plan outlining the steps to be taken in the event of a ransomware attack, including containment, eradication, recovery, and communication procedures. Test the plan regularly through tabletop exercises and simulations to ensure readiness.