Play ransomware, also known as PlayCrypt, is a sophisticated and evolving threat that emerged in 2022.
This ransomware group has garnered attention for its global impact, employing a double-extortion model wherein it encrypts systems after exfiltrating sensitive data. The group’s tactics, techniques, and procedures (TTPs) have undergone continuous refinement, making it a notable player in the ransomware landscape.
Play ransomware overview
Recent developments indicate that Play has expanded its focus to target managed service providers (MSPs) globally.
This campaign involves the use of intermittent encryption, where only parts of a file are encrypted, potentially to evade detection.
In a significant evolution, Play has also transformed into a Ransomware-as-a-Service (RaaS) operation. The group reportedly offers its ransomware services to other threat actors, indicating a level of collaboration and sophistication in the cybercriminal ecosystem.
The group’s targets include midsized businesses in finance, legal, software, shipping, law enforcement, and logistics sectors globally.
How to identify Play ransomware: Main IOCs
Indicators of compromise (IOCs) are pieces of forensic data that can help identify malicious activity or malware associated with a cyber attack. It includes the encryption extension, file hashes, and IP addresses, among other details cyber criminals leave as they infect a machine or system.
But, if you can’t identify the ransomware strain through its IOCs, you can use Proven Data’s free ransomware ID tool to check if the Play ransomware is the malware that encrypts your files.
Important: Some of these indicators require technical knowledge of the infected system, so you may need to contact your IT team or a digital forensics service provider.
Play ransomware-specific IOCs include:
File extension:
- .play
URLs:
- hxxp://84.32.190[.]37:80/ahgffxvbghgfv
- hxxp://newspraize[.]com
- hxxp://realmacnow[.]com
- 172.67.176[.]244
- 104.21.43[.]80
- hxxp://67.205.182[.]129/u2/upload[.]php
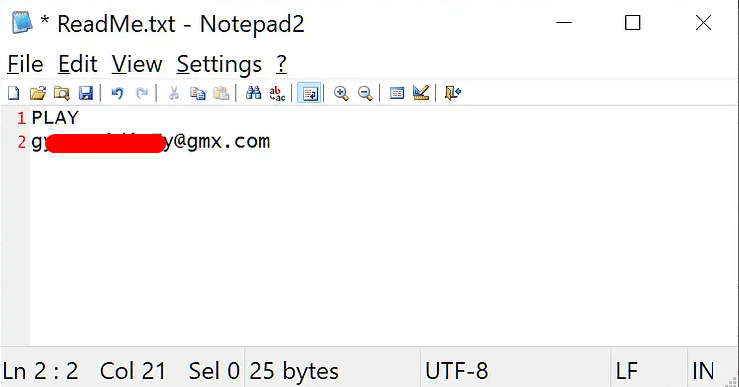
Ransom note:
- ReadMe.txt
Play ransom note
Play ransomware does not add an initial ransom demand or explicit payment instructions in its ransom notes. Instead, victims are directed to establish contact with the threat actors through email.
The ransom note is generated at the root of the hard drive (C:).
The ransom note features a minimalistic approach, bearing the solitary word “PLAY” alongside the designated contact email address. Certain variations of the ransom note may incorporate additional details, such as a link to the Tor website alongside the email address.
How Play ransomware works
Play ransomware orchestrates a meticulously planned sequence of actions, spanning various stages, to accomplish its malicious objectives. This elaborate process involves:
1. Initial Access
1. Initial Access
Play ransomware employs diverse entry points, including leveraging valid accounts, exploiting vulnerabilities in Remote Desktop Protocol (RDP) servers, and taking advantage of weaknesses in Fortinet SSL VPN (CVE-2018-13379 and CVE-2020-12812).
2. Execution
2. Execution
The ransomware executes its malevolent code through the utilization of scheduled tasks, PsExec, and Windows Management Instrumentation Command-line (wmic). Group Policy Objects (GPOs) serve as conduits to disseminate ransomware executables extensively within the internal network.
3. Persistence
3. Persistence
Valid accounts acquired during the initial access phase are persistently utilized. The ransomware strategically places its executable in crucial Domain Controller shared folders (NETLOGON or SYSVOL) and triggers execution via scheduled tasks or PsExec.
4. Privilege Escalation
4. Privilege Escalation
Play ransomware leverages the powerful Mimikatz tool to extract high-privilege credentials from the volatile memory. Manipulation of accounts, including those elevated to the Domain Administrators group, becomes a key strategy for privilege escalation.
5. Defense Evasion
5. Defense Evasion
A spectrum of tools, including Process Hacker, GMER, IOBit, and PowerTool, is deployed to effectively disable antimalware and monitoring solutions.
Simultaneously, Windows built-in tools such as wevtutil or batch scripts are employed to eradicate any trace of the ransomware’s presence.
6. Credential Access
6. Credential Access
Mimikatz takes center stage, being employed to dump credentials either directly onto the target host or executed through command-and-control (C&C) applications like Empire or Cobalt Strike.
7. Discovery
7. Discovery
Play ransomware conducts a thorough reconnaissance of the Active Directory (AD) environment.
This is achieved through the strategic deployment of tools such as ADFind, Microsoft Nltest, and Bloodhound.
Enumeration of system information, encompassing hostnames, shares, and domain details, is systematically performed.
8. Lateral Movement
8. Lateral Movement
A range of tools is brought into play for lateral movement, including the Cobalt Strike SMB beacon, SystemBC (a SOCKS5 proxy bot), Empire (an open-source post-exploitation framework), and Mimikatz. These tools enable the ransomware to traverse the network efficiently.
9. Exfiltration
9. Exfiltration
Before initiating the ransomware deployment, Play ensures the exfiltration of sensitive data. WinRAR is harnessed to archive victim files, and these archives are subsequently uploaded to file-sharing sites. WinSCP, an SFTP client, facilitates the secure transfer of these exfiltrated files.
10. Impact
10. Impact
Upon completing its nefarious operations, Play ransomware leaves an indelible mark by encrypting files and appending the extension “.play” to them.
Furthermore, a distinctive ransom note named ReadMe.txt emerges, providing explicit instructions on how victims can establish contact with the attackers for the ransom payment.
Important: Do not pay the ransom. Paying the ransom does not guarantee that you will get your data back, and it may encourage the attackers to continue their criminal activities. Check our in-depth article on what happens if you pay the ransom.
How to handle a Play ransomware attack
It is important to note that handling a ransomware attack can be complex and requires expertise. Therefore, it is recommended to seek professional help from a reputable data recovery service, such as Proven Data to help you recover your data and remove the ransomware from your system.
You can also report the attack to law enforcement agencies, such as the FBI, and cybersecurity organizations to help prevent future attacks and catch the perpetrators.
We strongly recommend contacting cybersecurity services to handle ransomware attacks. Proven Data technicians not only retrieve ransomware-encrypted data but also create forensic reports and streamline incident response, minimizing your business downtime and financial loss.
Notable attacks by Play ransomware
A joint cybersecurity advisory from Australia and the U.S. estimated that Play has affected approximately 300 organizations worldwide as of October 2023.
Here are some of the significant incidents attributed to Play ransomware:
Xplain attack
The Play ransomware group targeted Xplain, a Bernese IT firm in Switzerland. The attack affected federal and cantonal government departments, including the cantonal police, Swiss army, customs, and the Federal Office of Police. Stolen data from Fedpol and the Federal Office for Customs and Border Security (FOCBS) was published on a dark web forum.
Globalcaja attack
Play ransomware targeted Globalcaja, a major Spanish bank with over 300 branches nationwide. The ransomware group claimed responsibility for the attack, stating that they had stolen private and confidential data, including client and employee documents, passports, and contracts. The bank activated security protocols to mitigate the impact.
Polycom data breach
On May 22, 2023, Play ransomware posted Polycom, a global communications firm based in the US, on their leak site. The group claimed to have obtained 600GB of data, including private and personal information, employee documents, social security numbers, IDs, passports, budget details, and financial information.
Argentina’s Judiciary of Córdoba
On August 13, 2022, Play ransomware targeted Argentina’s Judiciary of Córdoba, shutting down its IT systems, databases, and online portals. The attackers encrypted files with “.play” extensions and left a ransom note instructing the victims to contact them. This incident affected the judicial operations in the region.
How to prevent Play ransomware attacks
How to prevent Play ransomware attacks
Preventing Play ransomware attacks is always the best cybersecurity tactic. If you are a recent victim, you must follow these tips to avoid a new ransomware attack:
Keep your software up to date
Use reputable antivirus software
Use reputable antivirus software
Be cautious of suspicious emails
Even though there are no known cases of Play using phishing as an attack method, it’s important to exercise caution when dealing with emails from unfamiliar or dubious origins. Refrain from opening files or clicking on links within emails that you are not expecting or seem suspicious.
Do not download cracked software
Backup your data
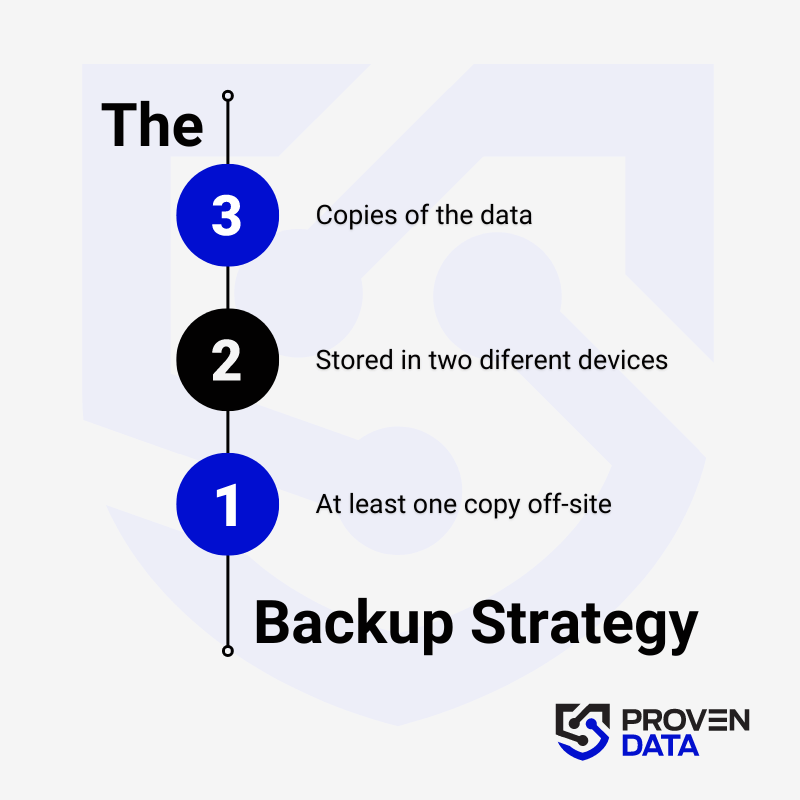
Regularly back up your data to an external hard drive or cloud storage service to prevent complete data loss in case of a ransomware attack. A highly recommended strategy for data loss prevention is the 3-2-1 backup strategy.
The 3-2-1 backup strategy involves creating three total copies of your data: two on different media and one offsite, ensuring redundancy and protection against data loss. And at least one copy offsite to prevent loss due to natural disasters or other local incidents.
Educate yourself and your teams
Educate yourself and your employees about the risks of ransomware and how to avoid it, such as avoiding suspicious emails or downloads.
Consult cybersecurity professionals
Proven Data offers cyber security services to help you keep your data protected against threat actors. From vulnerability assessment to ensure your systems and servers do not have open doors for cyber attacks, to Incident Response (IR) services for immediate response in case of a successful attack.
We also have the option of managed detection and response (MDR) services that help organizations improve their security posture, minimize risk, and protect sensitive data and assets