In recent years, there has been a tremendous increase in cyber attacks originating from phishing emails. Attackers are becoming more sophisticated in the crafting mechanisms to deploy malware on systems. This article will analyze the different ways that we have seen malware attack a system as well as it’s origins and how we can stay protected.
Where do phishing emails come from?
Based on our research, most of the IP addresses that we are seeing originate from Eastern Europe. Cybercriminals utilize various methods of malicious code injection through user activation. A common method is perceiving the user into inputting the password for the company’s email on a web server deployed by the hacker. We will explore two phishing emails that were received in the span of one day to our case management system, discover the origins, and the damage that this can cause to computer systems.
Do phishing emails steal passwords?
The first email we received is designed to persuade the recipient into thinking that the email comes from an authorized shipping center. It then describes that we have an available invoice and that our documents are available for pickup. Below is the screenshot of the email that was received.
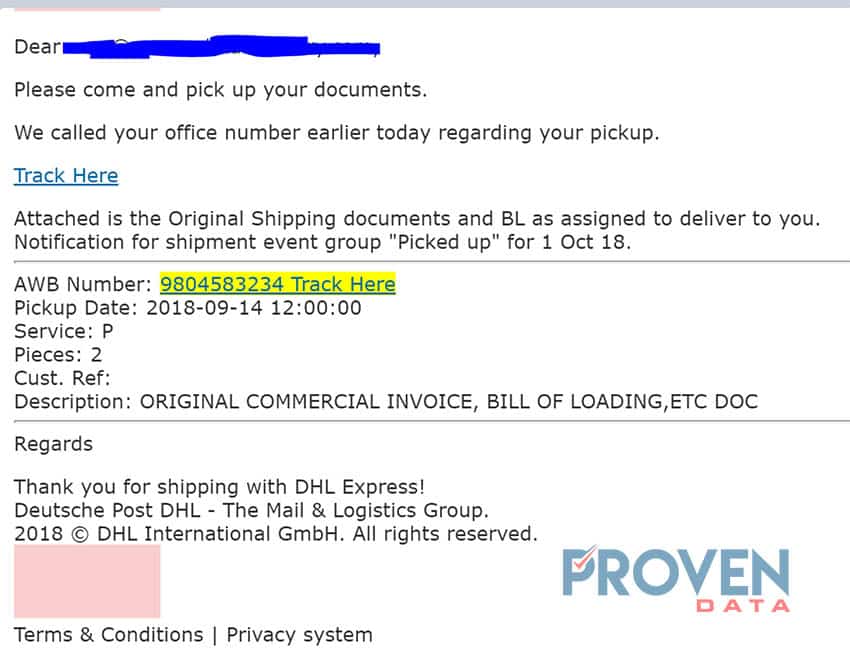
We can investigate this email further by using the link included in the email “Track Here”. Of course, we used a virtual machine with a sandbox environment in order to avoid damage to personal or company data.
The “Track Here” option contains a link to a malicious address. Upon entering the site in a sandboxed environment, we can see the following:
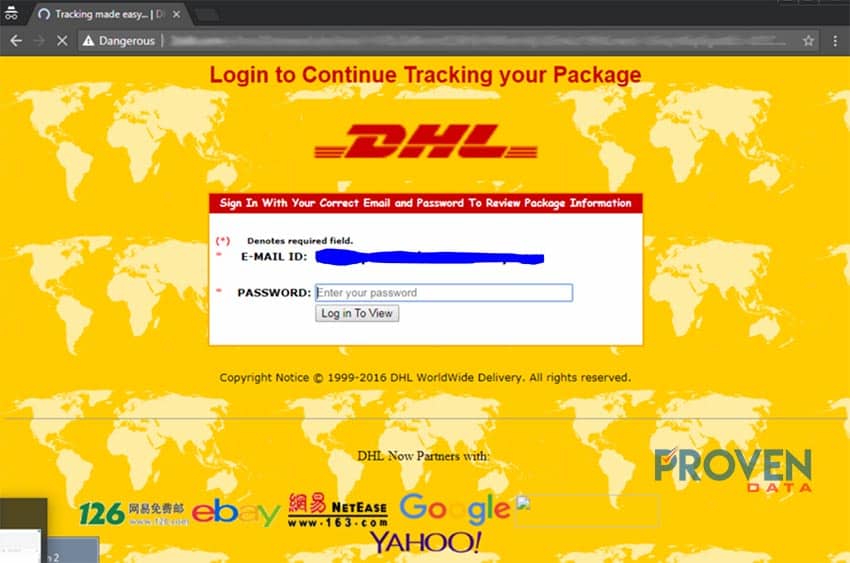
Upon analyzing the network traffic on Wireshark, we can see that the site used to communicate with the web server originates from the IP: 80.239.152.137 which is located in Switzerland. A more advanced hacker would most likely use a VPN or multiple Proxies to hide the true IP address of the web server. Moreover, an experienced hacker would place this server on a remote web hosting service in order to avoid detection. Therefore, we cannot conclude that the hacker’s location is currently in Switzerland.
Based on the information presented by the site, we can determine that this site will trick the victim into entering the password for a DHL account. The site will then capture the victim’s password and transfer it to a database in the attacker’s web server. This type of attack is very common when stealing user’s passwords as the sourced website can be cloned.
Users need to be educated about these attacks by looking at the sourced URL on their internet browser. The example below shows the internet browsers knows the website is dangerous.
![]()
Emotets and phishing emails
Emotet is a polymorphic banking trojan whose purpose is to steals banking information and send this information to an attacker. It can spread through infected phishing attachments to multiple computers and change its code over time.
The second phishing email received contains Emotet and it appears to be more realistic than the DHL site. It persuades users to believe that they have received a payment on one of their Chase accounts.
Below is a screenshot of the email received at one of our emails:
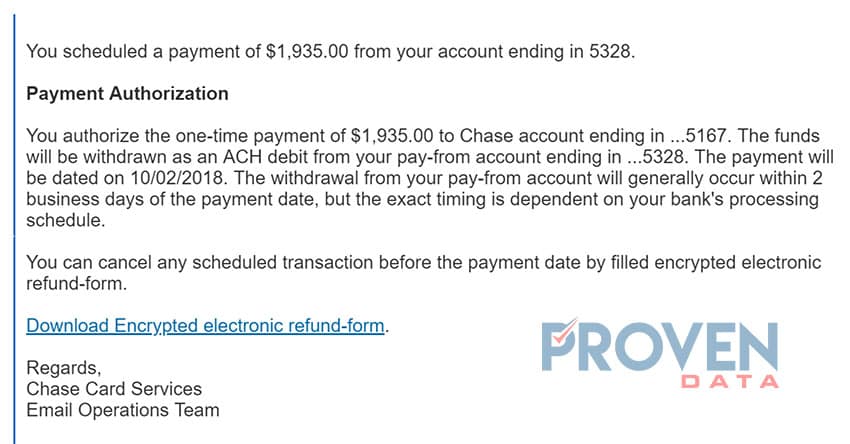
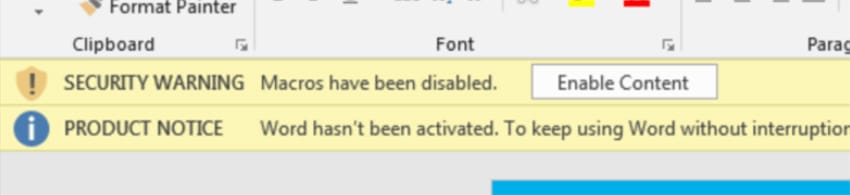
The email comes with a download link encouraging the user to click on this link to obtain the form with details of the payment. Upon opening this link, a file is automatically downloaded to the machine in a document called form-0407216657.doc. Thanks to Cisco Advanced Malware Protection (AMP) we can determine that this document contains an Emotet. Furthermore, this file uses macros to infect the system embedded into Microsoft Word. It asks for the victim’s permission to “enable editing” and “enable content”.
Below are screenshots of this process:
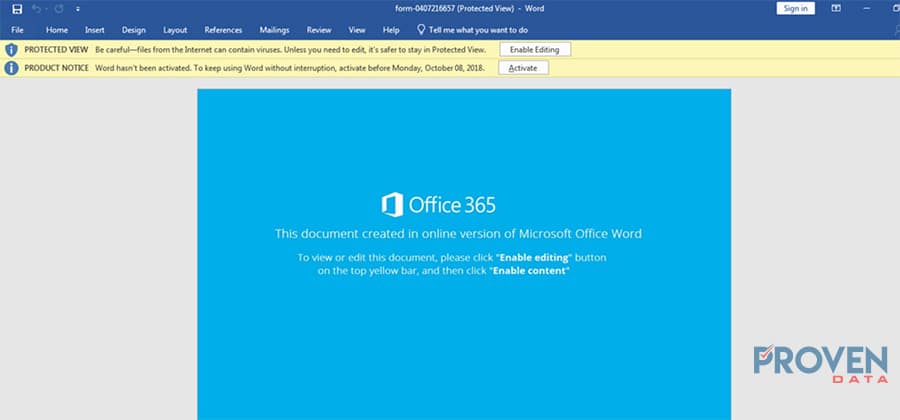
After the user clicks on “Enable Content”, the malware starts to execute in the background.
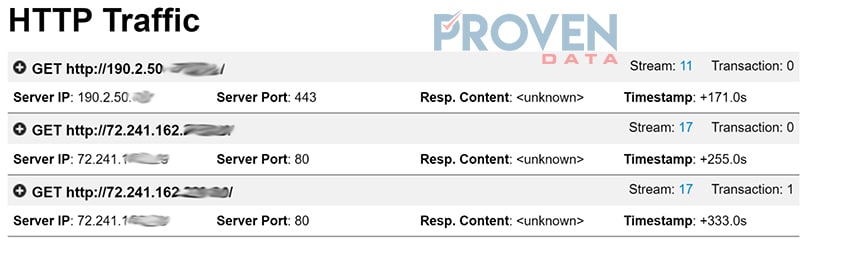
AMP detected that Form-0407216657.doc connects to various IP addresses with HTTP traffic including the following:
These IP addresses communicate directly with the Word document to further download additional files. One of these files is called “bearsneed.”Bearsneed is downloaded and placed in the Microsoft Windows AppData folder.
This file automatically starts to run as a process as demonstrated below:
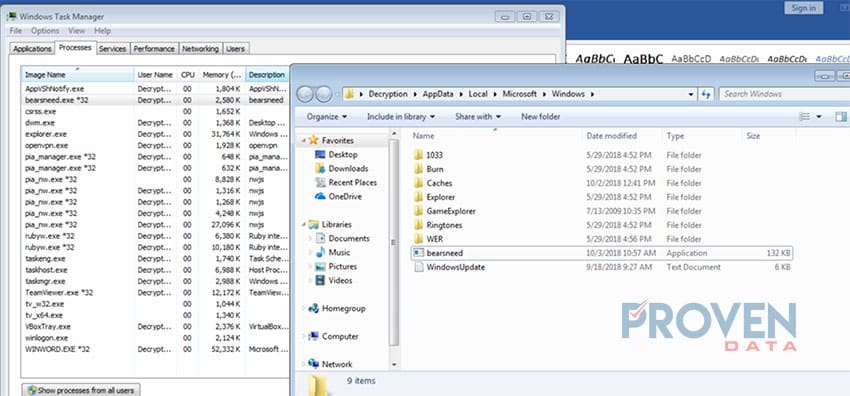
According to Cisco AMP threat intelligence, bearsneed.exe is the Emotet that runs in the background collecting banking information.
Bearsneed.exe also contains HTTP traffic to the following IP addresses:
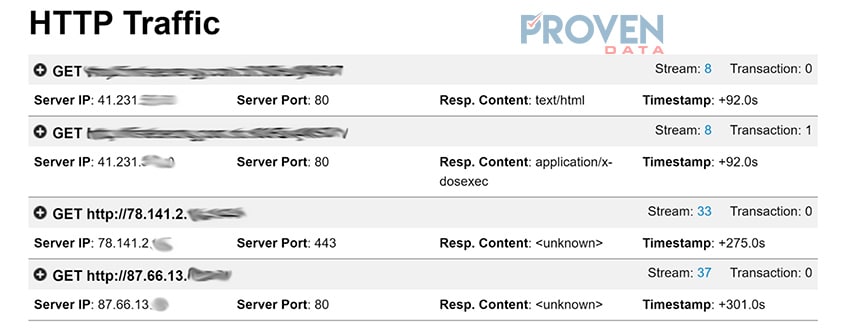
An uneducated user might follow the steps in the phishing email, click on the link to download that document, and follow all the steps to grant access causing widespread damages to the company’s infrastructure and data.
How do I stay protected from phishing emails?
Although the malware on the second email does not encrypt files on the system, it is an Emotet that can potentially steal banking information. Malicious sites can steal usernames and passwords which can later be used against the company. Moreover, an executed attachment can potentially open a shell console for the attacker to have remote access to the infected system through a Remote Administration Tool (RAT).
Therefore, we recommend users to be mindful of the emails that they receive containing suspicious attachments and links. A robust social engineering training should be in place for all companies to avoid attacks such as Phishing, Whaling, Baiting, and Vishing.
If you want to learn more about Social Engineering Training and cyber security costs for your company, please contact Proven Data.







