Elbie ransomware is a member of the Phobos crypto-virus family. This malware employs a complex encryption process, locking victims’ data and demanding a ransom payment for the decryption key.
The Elbie malware spreads mainly through spam email campaigns, disguised as seemingly legitimate communications from reputable entities.
In this comprehensive article, we will explore the Elbie ransomware variant in detail, and provide information on the indicators of compromise (IOC) associated with the group’s activity. It’s essential to understand which industries the ransomware targets and have some insight into how it operates to improve your cybersecurity and ransomware defense.
How to identify Elbie ransomware: Main IOCs
Indicators of compromise (IOCs) are pieces of forensic data that can help identify malicious activity or malware associated with a cyber attack. It includes the encryption extension, file hashes, and IP addresses, among other details cyber criminals leave as they infect a machine or system.
But, if you can’t identify the ransomware strain through its IOCs, you can use Proven Data’s free ransomware ID tool to check if the Elbie ransomware is the malware that encrypts your files.
Important: Some of these indicators require technical knowledge of the infected system, so you may need to contact your IT team or a digital forensics service provider.
Elbie ransomware-specific IOCs include:
File extensions:
- .id[12 alpha-numeric].[[email protected]].Elbie
- .Elbie
Email addresses used by attackers:
- decrypt2023@cock[.]li
- decrypt2023@cyberfear[.]com
Ransom note filenames:
- info.hta
- info.txt
- ##-IMPORTANT_NOTICE-##.Txt
Registry key (related to ransomware startup):
- C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\exec.exe
Commands to delete shadow copies:
- vssadmin.exe vssadmin delete shadows /all /quiet
- WMIC.exe wmic shadowcopy delete
Commands to disable recovery and repair functions of Windows:
- bcdedit.exe bcdedit /set default recoveryenabled no
- bcdedit.exe bcdedit /set default bootstatuspolicy ignoreallfailures
Commands to disable the firewall:
- netsh.exe netsh advfirewall set currentprofile state off
Command to launch ransomware requirements:
- mshta.exe “%USERPROFILE%\Desktop\info.hta
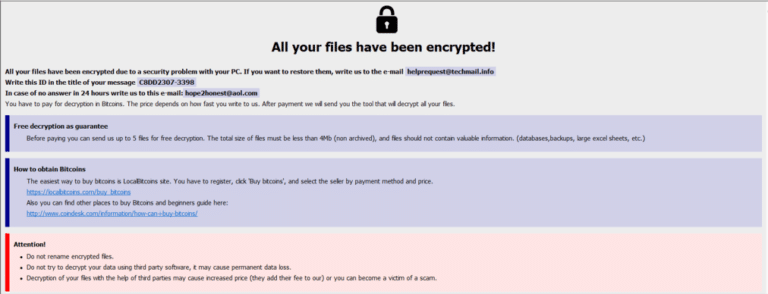
Elbie ransom note
After successful encryption, Elbie leaves a ransom note compelling the victims to reach out to the attackers through provided email addresses.
Sample of Elbie’s “info.hta” ransom note:
How Elbie ransomware works
Elbie operates silently, initiating its assault without displaying any symptoms during the initial stages.
The process of Elbie infection has several stages:
1. Initial Access
Elbie gains initial access through various methods, such as phishing emails, drive-by downloads, software cracking tools, or fake installers.
Phishing emails
Phishing emails involve deceptive messages sent to individuals, posing as trustworthy entities. These emails often contain malicious links or attachments designed to trick recipients into revealing sensitive information, clicking on links leading to malware downloads, or executing malicious scripts.
Drive-by downloads
Drive-by downloads occur when malware is automatically downloaded and installed on a user’s system without their explicit consent or knowledge. This can happen through visiting compromised websites or clicking on malicious ads. In this scenario, the ransomware payload is delivered and executed on the user’s system without their awareness.
Software cracking tools
Software cracking tools are unauthorized programs designed to bypass software licensing and activation mechanisms. While users may employ them to access premium features without payment, these tools often come bundled with malware.
Fake installers
Users may encounter fake installers on unofficial websites or through deceptive links, believing they are installing a genuine application.
2. Execution
Upon gaining access, Elbie uses a payload to execute a malicious script, initiating the installation of the ransomware on the victim’s system.
A payload is the malicious part of software or code that is designed to execute a specific set of actions on a target system.
In the case of ransomware like Elbie, the payload is the part of the malicious script or code that performs actions such as encrypting files on the victim’s system, communicating with a remote server, and generating unique keys for encryption. The payload is typically concealed within the broader structure of the malware and is activated upon execution.
3. Defense Evasion and Lateral Movement
Elbie employs defensive evasion techniques to avoid detection and removal. This could include disabling antivirus software or other security tools to operate undetected.
Seeking to escalate privileges further, Elbie aims to access credentials stored on the system. This could involve stealing login information, enabling the ransomware to move within the network.
4. Data Encryption
The final stage involves the actual encryption of files on the victim’s computer using AES-256 combined with RSA-1024 Asymmetric Encryption.
The ransomware appends the victim’s ID, email address, and the “.Elbie” extension to filenames. Subsequently, Elbie generates two ransom notes, “info.hta” and “info.txt,” informing victims of the encryption and the necessity to contact the attackers for the decryption tool.
Important: Do not pay the ransom. Paying the ransom does not guarantee that you will get your data back, and it may encourage the attackers to continue their criminal activities. Check our in-depth article on what happens if you pay the ransom.
How to handle an Elbie ransomware attack
It is important to note that handling a ransomware attack can be complex and requires expertise. Therefore, it is recommended to seek professional help from a reputable data recovery service, such as Proven Data to help you recover your data and remove the ransomware from your system.
You can also report the attack to law enforcement agencies like the FBI and cybersecurity organizations to help prevent future attacks and catch the perpetrators.
We strongly recommend contacting cybersecurity services to handle ransomware attacks. Proven Data technicians not only retrieve ransomware-encrypted data but also create forensic reports and streamline incident response, minimizing your business downtime and financial loss.
How to prevent ransomware attacks
Preventing Elbie ransomware attacks is always the best cybersecurity tactic. If you are a recent victim, you must follow these tips to avoid a new ransomware attack:
Keep your software up to date
Regularly update your operating system and programs to uphold security standards. Reputable OS providers will consistently check their software for vulnerabilities and patch their security standards to protect against newly detected threats.
Use reputable antivirus software
Employ reputable antivirus software to bolster protection against malware significantly, and regularly check that it is updated. You can also check your network for vulnerabilities and learn where to improve your security system.
Be cautious of suspicious emails
Even though there are no known cases of Elbie using phishing as an attack method, it’s important to exercise caution when dealing with emails from unfamiliar or dubious origins. Refrain from opening files or clicking on links within emails that you are not expecting or seem suspicious.
Do not download cracked software
Cracked software is the term used to describe illicitly modified or pirated versions of commercial software, typically distributed without proper authorization or licensing. Cybercriminals frequently conceal their ransomware executables within cracked software distribution websites, leading users to unwittingly download and execute the malware.
Backup your data
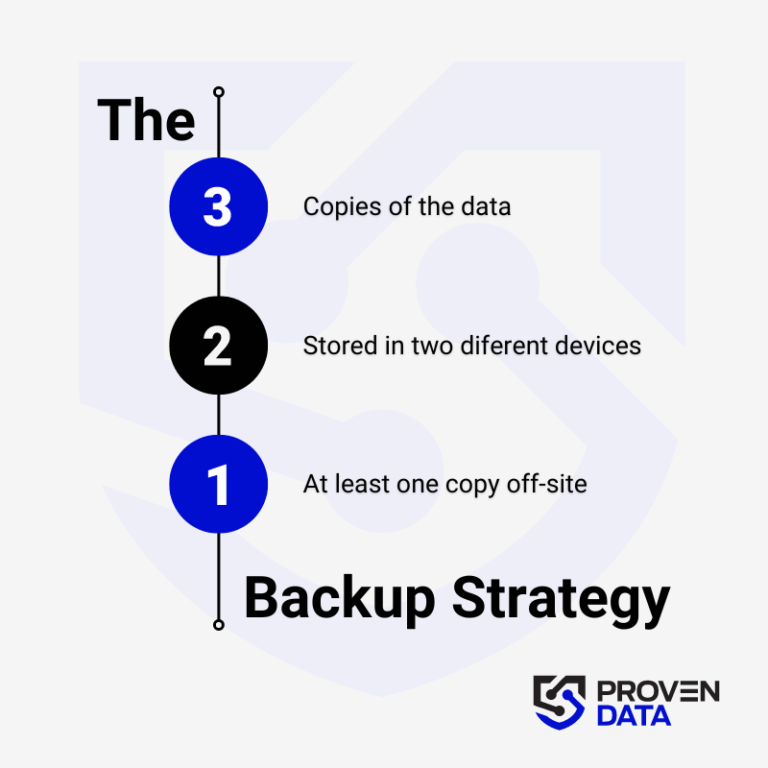
Regularly back up your data to an external hard drive or cloud storage service to prevent complete data loss in case of a ransomware attack. A highly recommended strategy for data loss prevention is the 3-2-1 backup strategy.
The 3-2-1 backup strategy involves creating three total copies of your data: two on different media and one offsite, ensuring redundancy and protection against data loss. And at least one copy offsite to prevent loss due to natural disasters or other local incidents.
Educate yourself and your teams
Educate yourself and your employees about the risks of ransomware and how to avoid it, such as avoiding suspicious emails or downloads.
Consult cybersecurity professionals
Proven Data offers cyber security services to help you keep your data protected against threat actors. From vulnerability assessment to ensure your systems and servers do not have open doors for cyber attacks, to Incident Response (IR) services for immediate response in case of a successful attack.
We also have the option of managed detection and response (MDR) services that help organizations improve their security posture, minimize risk, and protect sensitive data and assets.







