DragonForce is a ransomware-as-a-service (RaaS) operation that first gained public attention in 2023. It operates through a model in which core operators provide ransomware tooling and supporting infrastructure, while affiliates conduct intrusions and deploy ransomware. As a result, campaign execution can differ across affiliates.
Origin and evolution
DragonForce has been tracked as an active ransomware operation since 2023, emerging within the broader ecosystem of financially motivated extortion activity rather than ideology-driven disruption. Early ransomware campaigns associated with the DragonForce name lacked distinctive technical signatures or a clearly defined operational identity, instead reflecting patterns typical of newly established ransomware brands rather than a distinct, long-term technical profile.
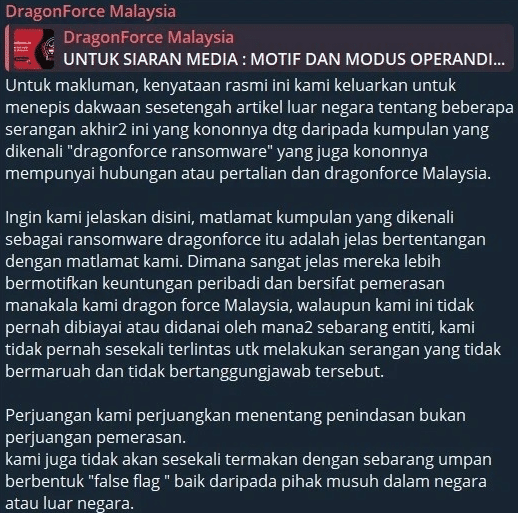
While the “DragonForce” name has also been used in reference to a Malaysian hacktivist group, publicly available information does not establish a verified technical or operational link between that activity and the later ransomware operation. A statement attributed to DragonForce Malaysia, circulated via its Telegram channel, disputes claims of a connection to “DragonForce ransomware,” so any direct continuity between the two should be treated as unproven rather than assumed.
As ransomware activity under the DragonForce label continued through 2023, campaigns showed significant variation in execution, infrastructure usage, and external presentation. Rather than consolidating into a single, cohesive threat actor, the DragonForce name increasingly functioned as a shared operational identity used across multiple extortion-focused campaigns. By 2024–2025, later incidents more consistently aligned around a recognizable extortion-driven pattern, indicating a shift toward a more structured operational framework, even as intrusion methods and execution details continued to vary across incidents.
Technical profile: platforms, encryption, and execution artifacts
Supported platforms and infrastructure
DragonForce ransomware has been deployed across common enterprise environments, including Windows systems, Linux servers, virtualized infrastructure such as VMware ESXi, and network-attached storage (NAS) devices. This cross-platform reach allows the ransomware to affect both user endpoints and shared infrastructure components within the same environment, depending on where execution occurs and how access is obtained.
Encryption mechanism
The ransomware employs encryption practices consistent with modern ransomware. File contents are encrypted using symmetric cryptography for performance, while the corresponding keys are protected through asymmetric encryption. This prevents recovery without the corresponding decryption material. Implementation details, including key handling and execution logic, can vary between builds and campaigns. Pre-encryption routines commonly include terminating processes and services that can block file access during encryption.
File renaming and ransom note behavior
During encryption, DragonForce may rename files by appending a campaign-specific extension. Files may carry the .dragonforce_encrypted suffix, which indicates encryption activity.
Affected directories are also typically populated with a ransom note in plain text format. The note informs the victim that data has been encrypted and provides instructions for contacting the attackers to negotiate recovery. Ransom notes often use generic file names such as README.txt. File names can differ across incidents.
Double-extortion support
Beyond simple system locking, DragonForce utilizes a double-extortion strategy. This involves two layers of pressure:
- System Encryption: Standard locking of business-critical files.
- Data Exfiltration: The theft of sensitive information prior to encryption, followed by the threat of public disclosure on “leak sites” if the ransom is not paid.
Tactics, techniques & procedures (TTP): attack chain and tools
Initial access methods
DragonForce-affiliated intrusions typically begin through common enterprise entry points rather than a single distinctive technique. Access is often obtained through credential-focused social engineering (such as phishing), exploitation of exposed or vulnerable services, abuse of remote access mechanisms like RDP, and other credential-based paths such as password reuse.
Some reporting has described DragonForce-linked intrusions involving vulnerabilities in remote monitoring and management (RMM) software. One report described exploitation of SimpleHelp RMM vulnerabilities (CVE-2024-57726, CVE-2024-57727, CVE-2024-57728) in attacks affecting managed service providers and downstream customer environments.
This flexibility allows affiliates to tailor initial access strategies to the target environment rather than following a fixed delivery method.
Privilege escalation, credential theft, and lateral movement
After establishing an initial foothold, operators focus on expanding and stabilizing access. At this stage, operations commonly involve persistence, privilege escalation, credential harvesting, and lateral movement to gain administrative control over high-value systems. This behavior aligns with human-operated ransomware intrusions, in which operators conduct internal discovery to map systems and identify sensitive repositories before moving to data theft and final execution.
Data theft and extortion execution
Once sufficient control is established, the focus shifts toward monetization. Sensitive data is identified, collected, and staged for exfiltration using a mix of built-in administrative utilities and third-party tooling, before systems are prepared for coordinated ransomware deployment. Operators may also attempt to reduce interference from security controls prior to encryption; in some DragonForce-linked deployments, defense evasion has involved exploiting vulnerable drivers, such as truesight.sys or rentdrv2.sys, to terminate security processes.
The final stage follows an “encrypt-or-leak” extortion model, combining ransomware execution with the threat of public data disclosure through dedicated extortion infrastructure. In reported incidents, this model can involve the theft and exfiltration of sensitive data before the encryption payload is triggered. Extortion is then managed through a dedicated negotiation workflow routed via a Tor-based portal, centralizing communications for the RaaS operation.
Notable attacks and victims
Since its emergence, the DragonForce name has been associated with incidents across multiple sectors, including public entities and major retailers. The case studies below summarize publicly reported events and the types of disruption described in reporting and official statements.
Ohio lottery cybersecurity incident
In late December 2023, the Ohio Lottery reported a cybersecurity incident that caused temporary outages as unauthorized access was investigated. A threat actor using the DragonForce name later claimed responsibility and alleged data theft; however, the Ohio Lottery’s public statements did not confirm attribution to a specific ransomware operation.
Yakult Australia data exposure
In December 2023, a cyber incident at Yakult Australia was publicly reported after internal company data appeared online. Australian media coverage described claims made under the DragonForce name, including the publication of employee-related records and internal documents. Reporting focused on data exposure, while attribution relied primarily on the attacker’s own claims rather than official confirmation by authorities.
2025 high-impact attacks on UK retailers
In 2025, a cluster of high-impact cyber incidents affecting major UK retailers was linked in reporting to the DragonForce name. Marks & Spencer disclosed a significant cyberattack that forced it to suspend online clothing orders for nearly seven weeks, contributing to broader disruption across logistics and product availability. In comments reported by Reuters, the company’s chairman said M&S believed the activity was associated with the DragonForce ransomware operation and that the incident was expected to cost roughly £300 million in operating profit. During the same period, incidents also affected other UK retailers, including Co-op and Harrods.
National crime agency investigation and arrests
In July 2025, the UK’s National Crime Agency announced the arrest of four suspects in connection with cyberattacks targeting Marks & Spencer, Co-op, and Harrods, reinforcing that these incidents were treated as a coordinated, high-priority law-enforcement investigation.
Affiliates, RaaS model, and ecosystem dynamics
Within the DragonForce ecosystem, operational responsibility is distributed across multiple independent actors, while shared elements are concentrated in extortion infrastructure, negotiation workflows, and branding. Affiliate turnover enables campaigns to continue over time, and campaign execution can vary across incidents even when the extortion framework remains consistent.
In addition, closely related payloads or infrastructure may appear under alternative labels while relying on the same underlying platform. This can complicate public tracking and attribution, and it may create uncertainty for victims and responders, as negotiation behavior, timelines, and pressure tactics can vary across affiliates.
Impact on organizations and operational risk
DragonForce-linked incidents demonstrate that ransomware impact extends beyond file encryption, with outcomes shaped by industry, scale, and operational context. Retail-focused attacks highlighted how downtime alone can disrupt logistics, inventory management, and customer-facing services, while incidents involving public-sector or data-centric organizations emphasized reputational damage and the exposure of sensitive information.
Attribution challenges and naming confusion
DragonForce activity reflects a broader challenge in modern ransomware tracking: attribution is often complicated by shared infrastructure, affiliate turnover, and inconsistent branding across campaigns. Incidents linked to DragonForce do not always present as a single, uniform operation, which can make early identification and classification difficult during an active response.
Across reported incidents, attacks attributed to DragonForce have often been associated primarily through attacker claims or leak-site activity rather than immediate technical confirmation. In others, attribution has emerged later through victim disclosures, investigative reporting, or law-enforcement action. This variability reflects how responsibility is distributed across different actors, reducing the reliability of naming alone as an indicator of scope or origin.
Detection, prevention, and response recommendations
Prevention and hardening
Reduce exposure and limit blast radius by enforcing MFA for remote access and privileged accounts, tightening control over externally exposed VPN and RDP endpoints, and segmenting networks so a single compromised host cannot easily reach core services.
To reduce exposure to BYOVD-style defense evasion reported in some DragonForce-linked deployments (including abuse of vulnerable signed drivers to disable security tooling), organizations should consistently enforce kernel-level protections. Enabling Hypervisor-Protected Code Integrity (HVCI) enforces Microsoft’s vulnerable driver blocklist and helps prevent the loading of known abused or vulnerable signed kernel drivers. In enterprise environments, similar controls can be deployed through App Control for Business policies aligned with Microsoft’s recommended driver block rules.
Maintain offline or immutable backups of critical systems, separate backup access from everyday administrative accounts, and regularly test restoration against your most important business services. Harden common entry paths by strengthening email and attachment controls, limiting execution from user-writable locations through application allowlisting, and reducing the use of high-risk scripting and macro-enabled content where it is not operationally required. Keep internet-facing systems and remote access infrastructure on a disciplined patching and configuration management cycle.
Detection and monitoring
Prioritize behavior-based detection over static indicators. Monitor for suspicious authentication patterns, unexpected privilege escalation, new persistence mechanisms, and lateral movement from user endpoints into server or directory environments. Centralize security logs, ensure adequate retention, and tune alerting for abnormal administrative activity and unusual outbound data transfer patterns that can precede exfiltration or encryption. On compromised systems, this may include a plain-text ransom note left in affected directories, alongside widespread file changes consistent with encryption activity.
Response and recovery
Contain incidents quickly while preserving key evidence for scoping. Isolate affected systems, capture relevant logs and volatile artifacts when feasible, and assume credentials may be compromised. Revoke active sessions, rotate passwords, and review privileged access paths. Scope the environment for related activity. Restore operations from verified backups when appropriate, and remediate the specific access paths and control gaps that enabled the intrusion. Validate recovery with targeted testing and document lessons learned to improve readiness before the next event.
Practical takeaways
DragonForce illustrates how modern ransomware operations can involve uncertainty around scope, responsibility, and data exposure. That structure can make campaigns harder to predict and allows similar operational patterns to resurface across different incidents and sectors.
For organizations, the key lesson is that resilience cannot rely on narrow assumptions about how attacks “usually” unfold. Ransomware risk spans identity, access control, data integrity, and operational continuity, and recovery often extends beyond reversing encryption. Even with backups, teams may need to validate system trust and reduce residual risk before restoring operations at scale. In complex incidents, this effort may involve Digital Forensics & Incident Response (DFIR) services or specialized ransomware data recovery experts to support controlled recovery and operational continuity.