Dire Wolf is a human-operated ransomware operation first documented in 2025 and linked to targeted, financially motivated intrusions. Dire Wolf uses a double-extortion model, combining system encryption with the threat of data exposure to increase pressure on victims.
Emergence and Observed Activity
Dire Wolf first surfaced in May 2025. It quickly established a presence through a dedicated dark web leak site for publishing victim disclosures. Activity has been observed across multiple regions and industry sectors, with technology and manufacturing repeatedly appearing among affected organizations. Victim disclosures on the group’s leak site have been published in batches, reflecting campaign-driven extortion activity.
Operating model
Dire Wolf’s operating model centers on controlled, operator-driven execution rather than automated spread. The workflow is designed to move from initial access to negotiated pressure through a structured extortion process built around direct communication and deliberate victim selection.
Double extortion mechanism
Dire Wolf uses a double extortion model that combines system encryption with data theft. Encryption is used to disrupt operations, while stolen data is leveraged through the threat of public exposure. The risk of disclosure adds reputational and legal pressure along with downtime, increasing leverage during negotiations.
Communication channels
Victims are directed to one-to-one negotiation through instructions in the ransom note. Communication is conducted through Tox, and a dedicated leak site supports pressure by providing a public venue for disclosure if demands are not met.
Targeting strategy
Dire Wolf’s victim set spans multiple countries and industries, with repeated impact across multiple commercial sectors. Target selection centers on operational and business leverage, prioritizing organizations where downtime and data exposure can create immediate, measurable costs.
Technical profile
Dire Wolf is a Go-based Windows encryptor commonly delivered as a UPX-packed executable. It is designed for controlled deployment in targeted intrusions, with execution logic focused on predictable completion and consistent behavior in enterprise environments.
Implementation and execution flow
Dire Wolf enforces basic guardrails to avoid unstable or redundant execution. It uses a system-wide mutex to prevent multiple instances from running simultaneously and checks for a local marker file to determine whether the host has already been processed. If either condition is met, execution stops.
This design limits re-encryption, reduces operational noise, and maintains consistent outcomes across repeated operator attempts.
Targeting scope and encryption behavior
When launched without a specific path, Dire Wolf enumerates attached storage and encrypts data across local storage and accessible network resources, depending on execution context. When a directory target is provided, encryption is scoped to that path and its subfolders.
The encryptor applies exclusion logic to skip critical operating system and stability-related directories and file types, preserving basic system operability after impact.
Encrypted files are marked with the .direwolf extension.
Cryptography and performance strategy
Dire Wolf implements a modern hybrid encryption design. It uses Curve25519-based key exchange with ChaCha20 for file encryption, generating per-file session keys. Smaller files are fully encrypted, while larger files may be partially encrypted by processing only an initial segment. This approach accelerates execution while rendering business-critical data unusable.
Post-execution hygiene
After encryption completes, Dire Wolf records the local completion state and may remove the encryptor from disk through self-deletion. Some executions also trigger a forced reboot, reducing the availability of in-memory artifacts after impact.
Pre-encryption disruption
Dire Wolf intrusions can include preparation steps taken before encryption to weaken recovery options and complicate restoration. These actions make restoration slower and scoping harder once systems are encrypted.
Backup and recovery interference
Before encryption, activity may focus on weakening restore paths by disrupting backup and recovery capabilities. This includes interrupting services and components commonly relied on for rapid restoration and business continuity, as well as actions that prevent or degrade local recovery features. By reducing the effectiveness of backups, snapshots, or automated restore workflows, attackers increase the likelihood that recovery will require manual rebuilding, validation, and extended downtime.
Forensic impact
Dire Wolf activity can also degrade forensic clarity by reducing logging around key execution windows. This includes suppressing or disabling Windows event logging, complicating timeline reconstruction, hindering confirmation of attacker activity, and limiting clear scoping of the compromise. When logging is degraded, responders must rely more heavily on endpoint state, network telemetry, and manual validation, which slows containment and increases investigation cost.
Once preparation and encryption are complete, the operation transitions into a structured extortion workflow.
Extortion workflow
Dire Wolf’s extortion workflow is structured around staged negotiation phases and time-bound escalation, combining encryption-driven disruption with controlled data-publication pressure.
Ransom note and initial contact
After encryption, Dire Wolf drops a ransom note commonly named HowToRecoveryFiles.txt. The note states that files have been encrypted and data has been taken, then introduces a short confidentiality window at the start of negotiations. It provides instructions for initiating contact via a private channel and references proof of access to stolen data through a sample file.
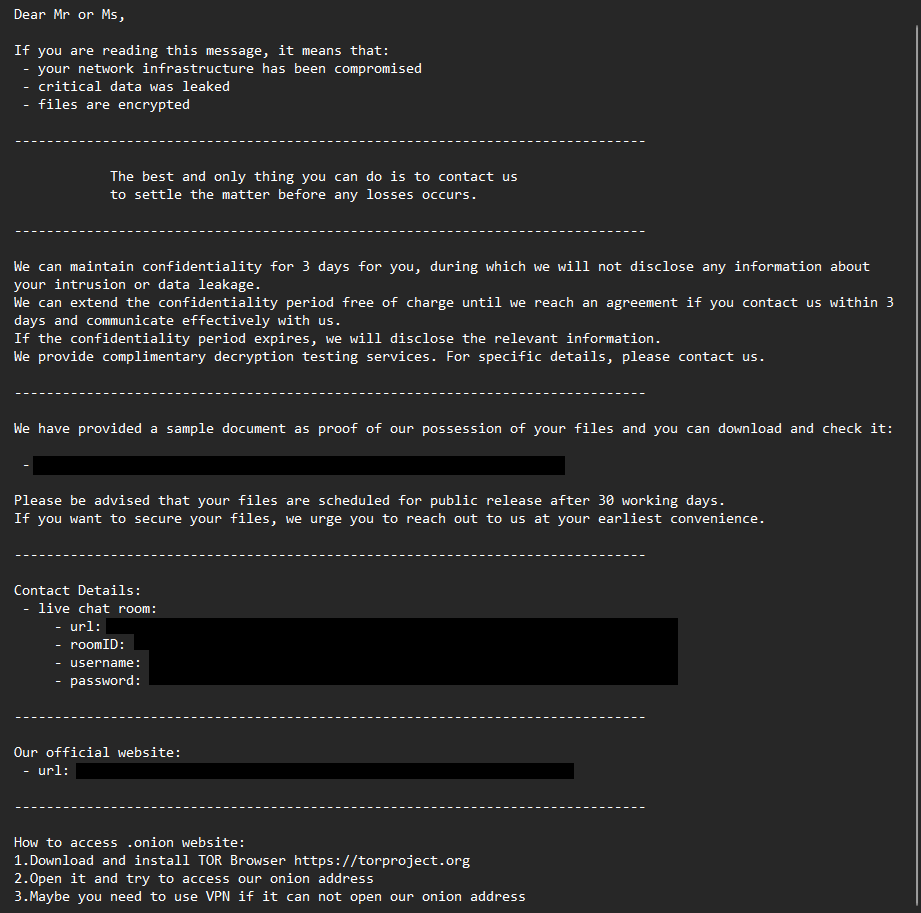
Negotiation channels and timelines
Negotiations are conducted one-to-one through Tox using victim-specific access details. The note defines explicit time pressure, including an initial confidentiality window followed by staged deadlines that accelerate engagement and structure escalation if negotiations stall.
Data leak site use
The leak site functions as the public escalation layer. Victims may be listed to increase urgency and demonstrate the credibility of the data-theft claim, often accompanied by a limited proof sample. If negotiations fail or deadlines expire, the workflow escalates toward broader disclosure, increasing legal and reputational exposure beyond the immediate operational impact of encryption.
Detection and threat hunting
Detection of Dire Wolf activity is most effective when focused on behavior rather than static indicators. Intrusions leading to encryption typically involve a short preparation phase in which visibility and recovery are deliberately degraded before destructive activity begins.
Early intrusion and pre-encryption warning signs
Hunting should prioritize administrative actions that degrade monitoring and resilience in the lead-up to disruption. High-signal events include suppressing or disabling Windows event logging, clearing event logs, and coordinated stopping of critical services that support backup, recovery, or system availability. These actions are rarely part of routine maintenance when they occur together and close in time.
Another strong warning pattern is clustered privileged activity that does not align with normal operations. This includes the sudden use of administrative tools on servers or file systems shortly after visibility is degraded or critical services are interrupted. Correlating privilege use with service disruptions and logging changes is often the earliest reliable signal of ransomware preparation.
Encryption onset indicators
When encryption begins, detection shifts from early warning to rapid confirmation and containment. High-rate file modification events across user and shared data locations, the appearance of the .direwolf file extension, and the presence of the ransom note HowToRecoveryFiles.txt are direct indicators that encryption is in progress or has just completed. These artifacts should trigger immediate isolation and incident response rather than serve as primary hunting signals.
Practical threat hunting focus areas
Threat hunting should concentrate on systems and identities that enable fast enterprise impact: file servers, backup infrastructure, domain controllers, and administrative workstations. The most reliable detections come from correlating multiple weak signals into a single sequence, such as brief preparatory activity followed by a sudden surge in file modifications.
In parallel, hunters should watch for identity conditions that enable rapid spread and impact, including unexpected administrative sessions, sudden privilege elevation, and the reuse of high-privilege accounts across multiple systems. These behaviors are consistent with the preparation phase of targeted ransomware operations and often precede visible encryption by only a short window.
Prevention and hardening
Reducing the impact of the Dire Wolf depends on limiting attacker leverage during the preparation phase and preserving recovery and visibility even when an intrusion reaches an advanced stage.
Backup isolation and recovery resilience
Because Dire Wolf actively weakens restore paths before encryption, the backup architecture is a primary control point. Backup repositories must be protected by separate administrative roles and restricted to a small, auditable set of accounts. Where feasible, immutable or offline storage models lower the risk that recovery data is modified or corrupted during the preparation phase. Equally important is recovery validation: regular testing of restore workflows ensures that snapshots and replicas remain usable during incidents and reduces the likelihood that recovery fails after encryption.
Identity and privilege control
Targeted ransomware relies on stable administrative access to prepare systems quietly before impact. Separating user accounts from administrative roles, enforcing multi-factor authentication on privileged access, and limiting the lifetime of elevated sessions directly reduce the window in which attackers can prepare systems without immediate detection.
Continuous review of standing administrative permissions and constraining the reuse of high-privilege accounts across servers, backup systems, and identity infrastructure limits the speed at which preparation actions can be executed at scale.
Service control and execution hardening
Dire Wolf preparation commonly involves disrupting critical services before encryption. Hardening should focus on restricting who can stop, disable, or reconfigure services related to backup, logging, and availability. Administrative actions against these services should be rare, centrally logged, and protected by approval or just-in-time elevation models. Execution hardening further constrains the transition from access to impact by enforcing application control on administrative systems, limiting execution from user-writable and temporary directories, and restricting the execution of uncommon installer and container formats.
Logging protection and visibility preservation
Because logging suppression directly degrades both detection and investigation, protecting logging infrastructure is a core resilience measure. Event logging services should be monitored for unauthorized stops, configuration changes, and log clearing. Centralized forwarding and protected retention limit reliance on local storage and preserve timelines even if endpoint visibility is degraded.
Securing log collectors and aggregation systems from the same administrative identities used on endpoints further limits the ability to suppress visibility across the environment in a single operation.
Network segmentation and blast radius reduction
Targeted ransomware benefits from flat administrative and data planes. Segmenting file servers, backup infrastructure, and administrative systems limits the number of systems that can be prepared and encrypted in a single operation. Separating backup identity from production identity and restricting east-west movement reduces the ability to disable recovery and encrypt large data sets in a short window.
Incident response considerations
Incident response for Dire Wolf should assume deliberate preparation, credential compromise, and partial degradation of visibility before encryption. An effective response depends on rapid containment, accurate scoping, and controlled recovery before broad remediation begins.
Containment and evidence preservation
The first priority is isolating affected systems to stop further attacker activity and prevent additional encryption. Containment should preserve system state where possible, including running processes and active network connections. Abrupt shutdowns or aggressive cleanup can destroy evidence needed to reconstruct the intrusion sequence.
Before large-scale remediation, responders should capture available logs, export volatile data, and preserve disk images of representative systems, especially in environments where logging visibility may already be degraded.
Credential and session management
Because targeted ransomware often relies on compromised credentials, identity must be treated as a primary control point during response. Active sessions should be revoked, authentication tokens invalidated, and high-risk credentials reset early in the process.
Responders should review delegated access, service accounts, and remote administration privileges to identify persistence paths that could allow re-entry after containment. Failure to neutralize identity access is a common cause of reinfection after endpoint cleanup.
Scoping and lateral movement analysis
Scoping should extend beyond the initially encrypted systems to determine how far the intrusion progressed before operations were disrupted. This includes identifying additional compromised hosts, tracing lateral movement paths, and locating persistence mechanisms established during the preparation phase.
Building a reliable timeline usually requires correlating authentication events, privilege changes, service modifications, and system state across multiple data sources, especially when logging visibility is incomplete.
Recovery and validation
Recovery should be staged and prioritized rather than simultaneous across the environment. Critical services and identity systems should be restored first using known-good baselines and verified recovery sources.
Before systems are returned to production, restoration should be validated by confirming that persistence mechanisms, unauthorized accounts, and malicious tooling have been removed, and that monitoring coverage is back in place.
Post-incident hardening
Once containment and recovery are stabilized, remediation should focus on closing the specific gaps that enabled access and preparation. Remove confirmed persistence paths, harden the initial access vector, tighten privileged access, and strengthen logging retention and tamper resistance to reduce the likelihood of recurrence.
Post-incident hardening should be driven by observed attacker behavior rather than relying solely on baseline or generic security controls.
Key takeaways
Dire Wolf shows how modern human-operated ransomware combines preparation activity, credential abuse, encryption, and data-exposure pressure into a managed extortion campaign. The practical takeaway is that resilience matters more than attribution, and outcomes depend on recovery readiness, identity integrity, and disciplined response once an intrusion is confirmed.
For organizations that want faster, more controlled action during a ransomware incident, an incident response retainer helps ensure rapid containment, evidence preservation, and coordinated decision-making. When the priority is restoring operations after disruption, ransomware recovery services focus on safe restoration and validation. They also reduce the risk of reinfection by addressing the access paths used in the intrusion.