INC ransomware is a ransomware-as-a-service (RaaS) operation that emerged in mid-2023 and rapidly established itself as a significant threat to organizations worldwide. The group employs double extortion tactics (stealing sensitive data before encrypting systems) to maximize pressure on victims. This article provides an overview of INC ransomware’s operational characteristics, attack lifecycle, and practical guidance for response, recovery, and prevention.
What is INC ransomware?
INC ransomware operates as a RaaS platform, meaning the core developers provide the malware and infrastructure while different actors conduct intrusions in exchange for a share of ransom proceeds. The operation involves multiple actors rather than a small fixed team, with revenue shared between operators and other participants.
The group is financially motivated with no confirmed ties to state sponsorship. Communications and tactics are consistent with Eastern European ransomware operations, though definitive attribution remains uncertain. INC maintains leak sites on the Tor network where victim data is published if ransom payments are not made.
A distinguishing characteristic is INC’s cross-platform capability. The ransomware targets Windows systems, Linux servers, and VMware ESXi virtualization environments, enabling broad impact across enterprise infrastructure. The Linux variant, first observed in December 2023, includes ESXi-specific functionality.
Relationship to Lynx ransomware
In mid-2024, a ransomware variant called Lynx emerged with significant code overlap – approximately 48% overall similarity and up to 70% similarity in shared functions. Lynx appears to be a successor to INC, with strong code and behavioral overlap. This transition coincided with the sale of INC’s source code on underground forums between March and May 2024.
Organizations should treat INC and Lynx as part of the same threat lineage. Detection rules and indicators developed for INC remain relevant to Lynx activity.
How INC ransomware attacks unfold
INC ransomware incidents follow a structured, multi-stage pattern consistent with human-operated ransomware campaigns. Understanding this lifecycle helps organizations identify intrusions before encryption occurs.
Phase 1: Initial access
Threat actors gain entry through several vectors. Phishing attacks targeting employees remain a common method, often delivering malicious attachments or credential-harvesting links. Stolen credentials purchased from underground markets or harvested by information-stealing malware provide another entry point.
Exploitation of vulnerabilities in internet-facing systems represents a significant access method. INC-related intrusions have leveraged CVE-2023-3519, a critical remote code execution vulnerability in Citrix NetScaler gateways. Some intrusions attributed to INC have involved exploitation of CVE-2023-48788, a SQL injection vulnerability in Fortinet FortiClient EMS.
Initial access brokers also play a role, selling pre-existing network access to ransomware operators. This allows attackers to bypass the intrusion phase entirely and proceed directly to internal operations.
Phase 2: Foothold and reconnaissance
After gaining access, attackers establish persistence and map the target environment. They employ living-off-the-land techniques, using built-in administrative tools to avoid detection. Commands such as net user /domain and net group /domain enumerate Active Directory accounts and groups.
Network scanning tools like Advanced IP Scanner identify additional systems. Attackers also query LDAP to inventory domain computers and locate critical assets, including domain controllers, file servers, and backup infrastructure.
Credential harvesting is central to this phase. Tools like Mimikatz extract credentials from memory, while custom scripts such as VeeamCreds.ps1 target credentials used by backup software. Obtaining backup system access serves dual purposes: enabling privilege escalation and preparing to neutralize recovery options.
Phase 3: Lateral movement and privilege escalation
Armed with harvested credentials, attackers propagate across the network. PsExec and Windows Management Instrumentation (WMI) enable remote command execution on additional systems. Remote desktop tools, including AnyDesk and TightVNC, provide persistent access to compromised hosts.
The objective is domain administrator access, which provides full control over the environment. Attackers may create new administrative accounts or add compromised accounts to privileged groups. Security tools are disabled where possible – Process Hacker and a custom tool called ProcTerminator have been observed terminating security processes.
Phase 4: Data exfiltration
Before encryption, attackers exfiltrate sensitive data to use as leverage. Target data includes customer records, financial information, intellectual property, and executive communications. Files are typically compressed using 7-Zip before transfer.
Exfiltration often occurs via cloud storage services. MegaSync, which uploads data to Mega.nz, is used for data exfiltration in multiple incidents. Large transfers may occur overnight to complete before encryption is triggered.
Phase 5: Encryption and extortion
With data stolen and access secured, attackers deploy the ransomware payload across the environment. The malware encrypts files on local drives, network shares, and virtual machine storage. To maximize speed, INC employs partial encryption – encrypting only portions of each file sufficient to render it unusable.
The ransomware uses AES-128 in CTR mode for file contents and Curve25519 elliptic-curve cryptography for key protection. Multi-threading accelerates the process, with the malware spawning threads proportional to the number of available CPU cores.
Ransom notes are delivered aggressively. Text and HTML files named “INC-README” appear in affected directories. The malware also attempts to print ransom messages to network printers and change desktop wallpapers. Encrypted files receive the .inc extension (or .LYNX in successor variants).
Victims are directed to Tor-based negotiation portals. The group maintains both a private communication site and a public leak blog where data is published if payment is not received.
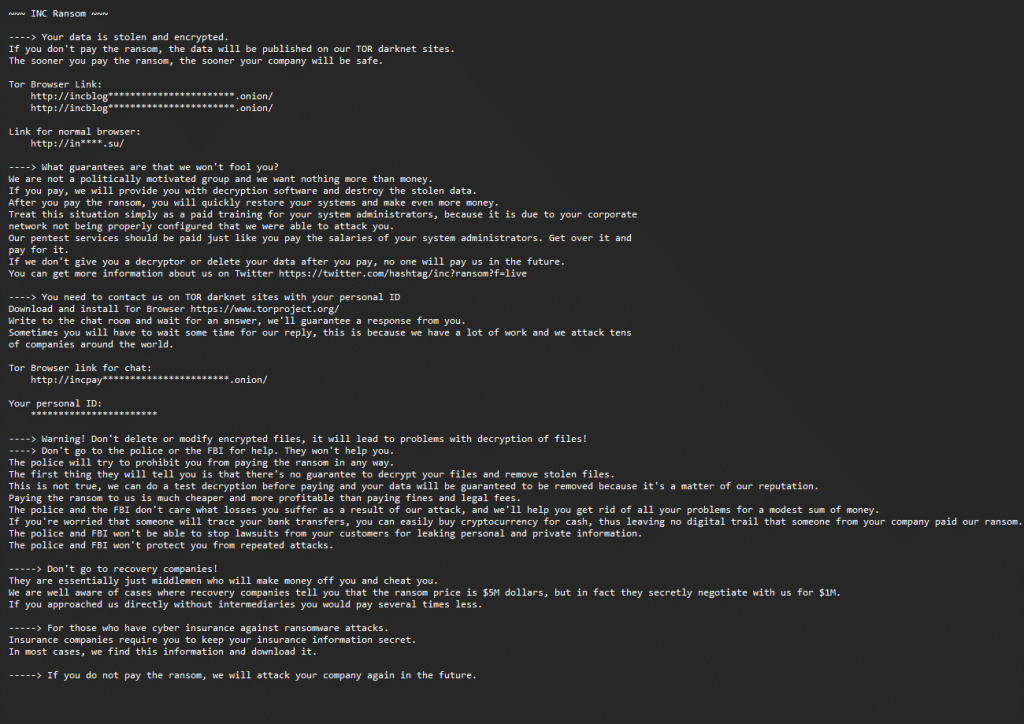
~~~ INC Ransom ~~~
—-> Your data is stolen and encrypted.
If you don’t pay the ransom, the data will be published on our TOR darknet sites.
The sooner you pay the ransom, the sooner your company will be safe.
Tor Browser Link:
http://incblog***********************.onion/
http://incblog***********************.onion/
Link for normal browser:
http://in****.su/
—-> What guarantees are that we won’t fool you?
We are not a politically motivated group and we want nothing more than money.
If you pay, we will provide you with decryption software and destroy the stolen data.
After you pay the ransom, you will quickly restore your systems and make even more money.
Treat this situation simply as a paid training for your system administrators, because it is due to your corporate
network not being properly configured that we were able to attack you.
Our pentest services should be paid just like you pay the salaries of your system administrators. Get over it and
pay for it.
If we don’t give you a decryptor or delete your data after you pay, no one will pay us in the future.
You can get more information about us on Twitter https://twitter.com/hashtag/inc?ransom?f=live
—-> You need to contact us on TOR darknet sites with your personal ID
Download and install Tor Browser https://www.torproject.org/
Write to the chat room and wait for an answer, we’ll guarantee a response from you.
Sometimes you will have to wait some time for our reply, this is because we have a lot of work and we attack tens
of companies around the world.
Tor Browser link for chat:
http://incpay***********************.onion/
Your personal ID:
***********************
—-> Warning! Don’t delete or modify encrypted files, it will lead to problems with decryption of files!
—-> Don’t go to the police or the FBI for help. They won’t help you.
The police will try to prohibit you from paying the ransom in any way.
The first thing they will tell you is that there’s no guarantee to decrypt your files and remove stolen files.
This is not true, we can do a test decryption before paying and your data will be guaranteed to be removed because it’s a matter of our reputation.
Paying the ransom to us is much cheaper and more profitable than paying fines and legal fees.
The police and the FBI don’t care what losses you suffer as a result of our attack, and we’ll help you get rid of all your problems for a modest sum of money.
If you’re worried that someone will trace your bank transfers, you can easily buy cryptocurrency for cash, thus leaving no digital trail that someone from your company paid our ransom.
The police and FBI won’t be able to stop lawsuits from your customers for leaking personal and private information.
The police and FBI won’t protect you from repeated attacks.
—–> Don’t go to recovery companies!
They are essentially just middlemen who will make money off you and cheat you.
We are well aware of cases where recovery companies tell you that the ransom price is $5M dollars, but in fact they secretly negotiate with us for $1M.
If you approached us directly without intermediaries you would pay several times less.
—–> For those who have cyber insurance against ransomware attacks.
Insurance companies require you to keep your insurance information secret.
In most cases, we find this information and download it.
—–> If you do not pay the ransom, we will attack your company again in the future.
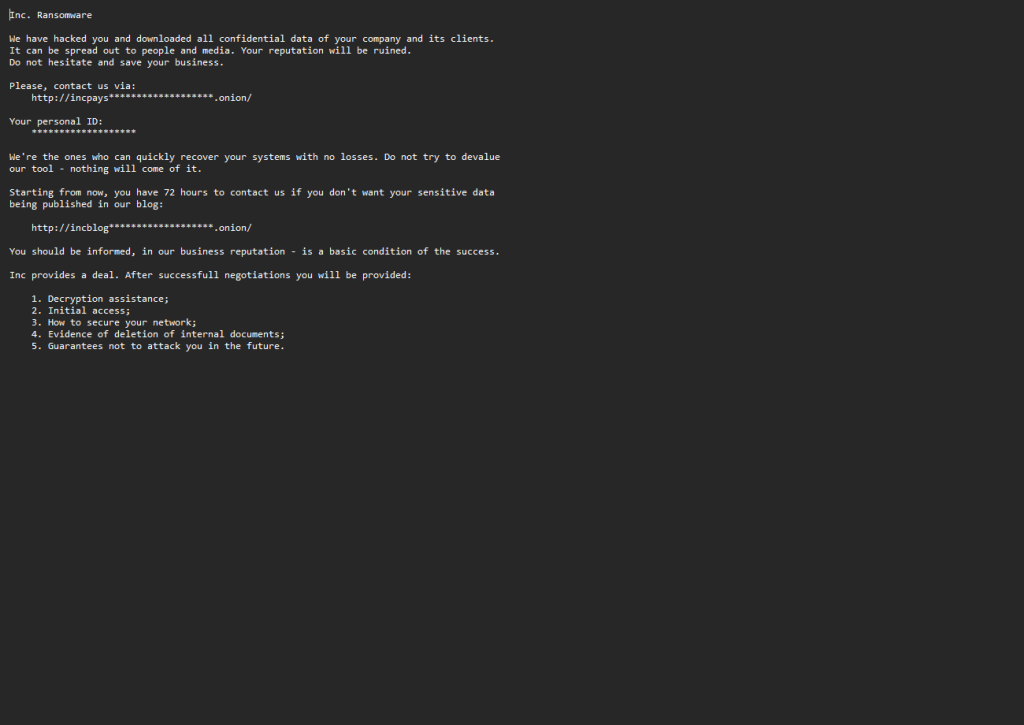
Inc. Ransomware
We have hacked you and downloaded all confidential data of your company and its clients.
It can be spread out to people and media. Your reputation will be ruined.
Do not hesitate and save your business.
Please, contact us via:
http://incpays*******************.onion/
Your personal ID:
*******************
We’re the ones who can quickly recover your systems with no losses. Do not try to devalue
our tool – nothing will come of it.
Starting from now, you have 72 hours to contact us if you don’t want your sensitive data
being published in our blog:
http://incblog*******************.onion/
You should be informed, in our business reputation – is a basic condition of the success.
Inc provides a deal. After successfull negotiations you will be provided:
1. Decryption assistance;
2. Initial access;
3. How to secure your network;
4. Evidence of deletion of internal documents;
5. Guarantees not to attack you in the future.
Who INC ransomware targets
INC ransomware has affected organizations across multiple sectors and geographies. Manufacturing and industrial companies are frequently targeted, likely due to their low tolerance for operational downtime. Professional services, technology firms, and healthcare organizations have also been affected.
Geographically, the United States accounts for a large share of disclosed victims, followed by the United Kingdom, Canada, Australia, and Germany. Incidents have been documented across Europe, Asia-Pacific, Latin America, and the Middle East. Notably, no publicly reported incidents have affected organizations in Russia or Commonwealth of Independent States countries, a pattern consistent with many Russian-speaking ransomware operations.
Target selection suggests deliberate reconnaissance. Victims tend to be medium to large enterprises with significant data assets, and the involvement of initial access brokers points to pre-selected, high-value targets.
Indicators of compromise (IOCs)
The following indicators are associated with INC ransomware activity:
- File Extensions: .inc, .INC, .LYNX
- Ransom Note Filenames: INC-README.txt, INC-README.html
- Exploited Vulnerabilities: CVE-2023-3519, CVE-2023-48788
- Associated Tools: Mimikatz, Process Hacker, PsExec, AnyDesk, 7-Zip, MegaSync, Advanced IP Scanner
- Behavioral Indicators: Volume Shadow Copy deletion, Safe mode boot manipulation, Mass termination of SQL, backup, and security processes, Unusual administrative account creation or group membership changes, Large outbound data transfers to cloud storage services.
Response and recovery
Organizations experiencing an INC ransomware incident should engage incident response resources immediately. The following framework provides guidance for containment through recovery.
Immediate containment
Isolate affected systems from the network by disconnecting cables or disabling switch ports. If encryption is actively spreading, network isolation may limit the scope of damage. Avoid powering off systems immediately if forensic evidence collection is possible; memory contains data critical to the investigation.
Disable or reset any accounts suspected of compromise, particularly those with administrative privileges. If domain administrator credentials were obtained, assume broad compromise and plan for a comprehensive credential reset.
Scoping the incident
Determine which systems were accessed and what data may have been stolen. Digital forensics analysis of compromised systems helps reconstruct the attack timeline and identify all affected assets. Review authentication logs, EDR telemetry, and network traffic records.
Assess data exposure by identifying which file shares and databases were accessible to compromised accounts. Network logs showing large outbound transfers indicate likely exfiltration.
Eradication and recovery
Rebuilding compromised systems from clean images is safer than attempting to clean infected machines, particularly for domain controllers and critical servers. All domain credentials should be reset, including the KRBTGT account (twice, per standard Active Directory breach procedures).
Remove any persistence mechanisms installed by the attackers, including unauthorized user accounts, scheduled tasks, services, and remote access tools.
Restore data from backups after validating backup integrity. Test restorations in an isolated environment before reconnecting to production networks. Return systems to production in stages, monitoring closely for signs of re-compromise.
Ransom payment considerations
Ransomware payment does not guarantee data safety. Attackers may retain copies of stolen data despite promises of deletion. The provided decryption tools may be incomplete or unreliable. Some jurisdictions restrict payments to sanctioned entities.
Organizations should evaluate payment decisions based on backup availability, operational impact, legal counsel, and law enforcement guidance. Engaging cyber insurance carriers early in the process is a critical part of how a company should handle a ransomware attack.
Prevention and hardening
Defensive measures should address the specific techniques observed in INC ransomware operations.
Identity and access controls
Enforce multi-factor authentication on all remote access points, including VPNs, RDP gateways, and cloud services. Review privileged accounts regularly and remove unnecessary access. Service accounts should use strong, unique passwords and operate with the minimum necessary privileges.
Monitor for unusual authentication patterns: logins from unexpected locations, off-hours access, or a single account authenticating across many systems in a short period.
Perimeter and vulnerability management
Prioritize patching for internet-facing systems. CVE-2023-3519 and CVE-2023-48788 should be addressed immediately where applicable. Reduce external attack surface by disabling unnecessary services and restricting RDP/SSH access from the internet.
Deploy web application firewalls and intrusion prevention systems to detect exploitation attempts against perimeter infrastructure.
Network segmentation
Segment networks to contain lateral movement. Domain controllers, backup servers, and sensitive file shares should reside on isolated VLANs with restricted access. Workstations should not have direct access to server subnets unless explicitly required.
Backup resilience
Maintain offline or immutable backups that ransomware cannot reach during an attack. Backup systems should use credentials separate from the primary domain. Test restoration procedures regularly to verify data integrity and measure recovery time.
Security checklist
The following actions address the INC ransomware attack patterns directly:
- Enforce MFA on all remote access (VPN, RDP, Citrix, cloud portals)
- Patch CVE-2023-3519 (Citrix NetScaler) and CVE-2023-48788 (Fortinet FortiClient EMS) if these products are deployed
- Restrict RDP and SSH exposure from the internet
- Segment domain controllers and backup servers on isolated VLANs
- Maintain offline or immutable backups with separate credentials
- Deploy EDR with detection for Mimikatz, PsExec, and VSS deletion
- Monitor for unusual admin account activity and off-hours authentication
- Block or monitor access to file-sharing services (Mega.nz) at the network perimeter
- Test backup restoration procedures quarterly
- Develop and rehearse a ransomware-specific incident response plan
- Have a reputable company on an incident response retainer
INC ransomware represents a capable and active threat that continues to evolve through its successor operation, Lynx. Organizations should monitor for tactical changes while maintaining defenses against the established attack patterns described above. Early detection during the reconnaissance and lateral movement phases offers the best opportunity to contain incidents before encryption occurs.